How to Check the Health State of Microsoft Sentinel
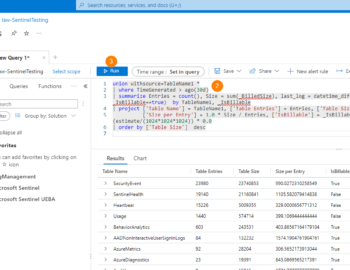
Now that you have it deployed and collecting data, how to you monitor the health state of all the connectors and rules? One of the challenges with Sentinel is that this is often overlooked and data connectors can go days or weeks missing valuable logs without detection. In this post, we look at how to make your data collection more robust and create a way to tell you about broken tooling.