Incident Response Foundations – Identity
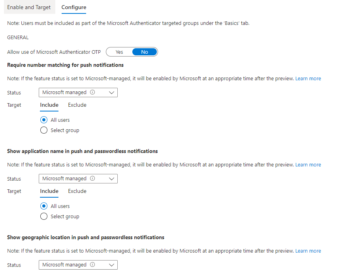
In today’s post I talk about responding to a compromised identity in Microsoft Entra ID. There is a lot of advice floating around on what to do and how to respond; I’m bringing experiences and existing guidelines together to provide a solid foundational starting point for identity based incident response in this post.