
Microsoft Sentinel Governance Deep-Dive Part 2
This week continues our look at an ongoing set of Governance tasks that we can do to keep our Sentinel instances working smoothly and helping our SOC team stay focused on handling Incidents and threat hunting. Today we continue our detailed look at not only what to review, but walking through the steps together. In today’s article we will review even more deep-dive details on how to optimize and maintain your Sentinel instances in a meaningful and optimized fashion. This week, we talk data management, automations, and RBAC.
I suggest getting caught up if you missed the first Deep-Dive article right here.
Last post bit off a big chunk of Sentinel Governance tasks and tips. Let’s continue that theme in this post with the next steps and what we can do to keep our Sentinel workspaces in tip-top shape! Let’s jump right in!
Log Analytics Workspace Review
Reviewing your Log Analytics Workspace periodically is always a good idea. I’ve heard storage accounts referred to as one of the easiest ways to forget how money is being spent in Azure…. A good way to keep a handle on that storage cost is to review it occasionally.
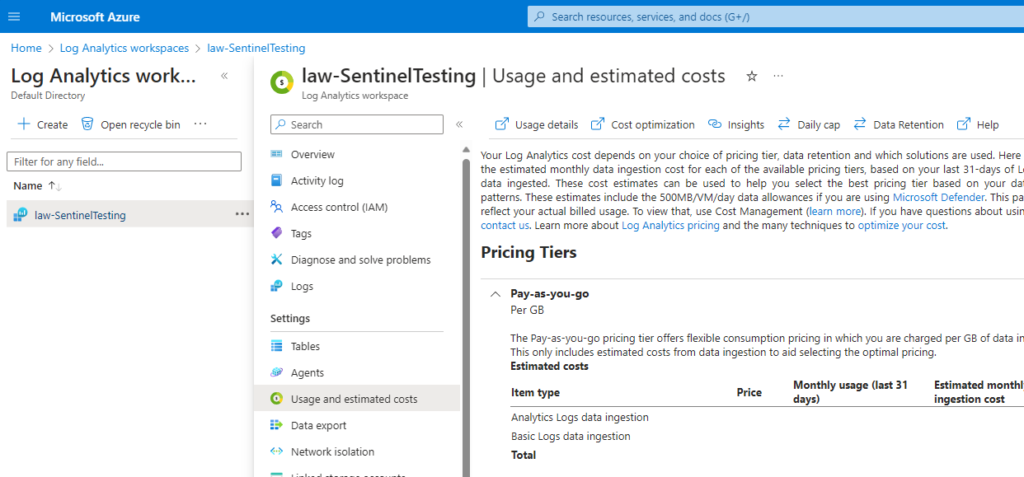
In the Azure Portal, go to Log Analytics Workspaces, choose your Sentinel workspace, then go to Usage and Estimated Costs. Take a look through and understand what data is coming in, how much and how long you are retaining data for. The question I always ask my clients is “Do you use this data?”. “How about this table data from 8 months ago? Do you use it still?”
Consider adjusting your overall retention to meet your business requirements and needs, but also your table data retention. We’ll talk about that in our next article in more depth!
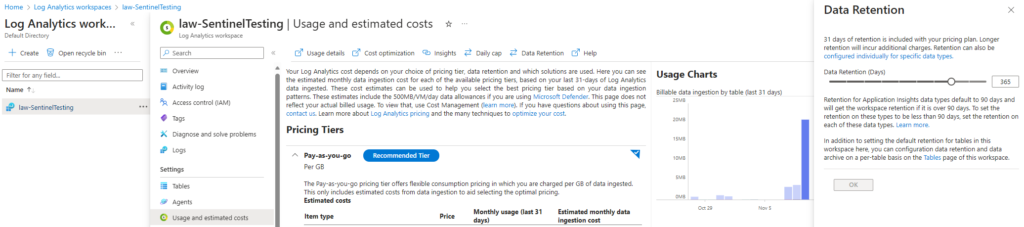
If you want to get a more granular understanding of what data is hiding in the log analytics workspace, try running this query:
union withsource=TableName1 *
| where TimeGenerated > ago(30d)
| summarize Entries = count(), Size = sum(_BilledSize), last_log = datetime_diff("second",now(), max(TimeGenerated)), estimate = sumif(_BilledSize, _IsBillable==true) by TableName1, _IsBillable
| project ['Table Name'] = TableName1, ['Table Entries'] = Entries, ['Table Size'] = Size,
['Size per Entry'] = 1.0 * Size / Entries, ['IsBillable'] = _IsBillable, ['Last Record Received'] = last_log , ['Estimated Table Price'] = (estimate/(102410241024)) * 0.0
| order by ['Table Size'] descNote that in the 2nd line you can adjust the “30d” to any length of time you wish to examine, and in the 2nd last line you can also adjust your cost per GB from the “0.0” to what your cost is in your tenant. Output from this query looks like this:
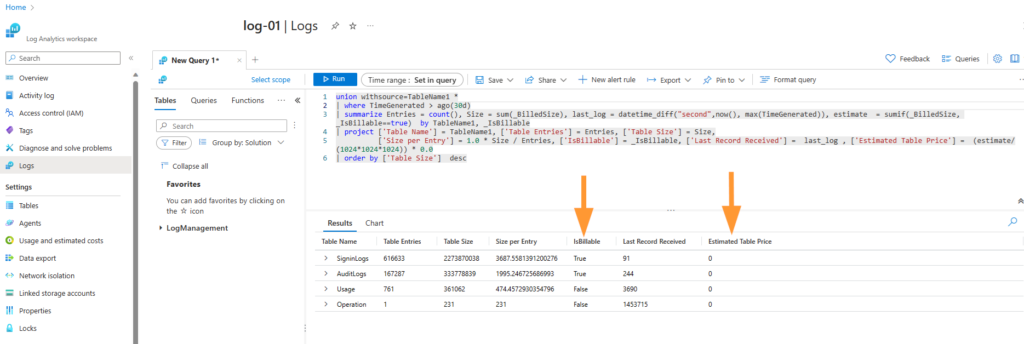
I don’t remember now where I came across this query, but I’ve used it and updated it for different needs for a few years now….knowing myself, it was likely in a Microsoft article somewhere.
Reviewing Automations
Another area to review regularly in Sentinel is your automations. There are quite a few different resources and tools to consider when we talk about automations and Sentinel:
- Automation Rules
- Custom connectors for logic apps
- Logic Apps
- Playbooks
- Azure Functions
- Azure & Security CoPilot upcoming functionalities
Let’s take a look at what we can quickly establish for automations in Sentinel:
In the Sentinel dashboard, select Automation under the Configuration heading. Next take a look at the top of that dashboard:
Select Automation Health Workbook.
The wonderful thing about this workbook is that you can use the underlying KQL and customize this to meet your own needs! Further, Microsoft shares the tables that we need to examine for automation health:
- ITEM – TABLES
——————————– - Automation Health – SentinelHealth
- Playbook Health (Azure Diagnostics) – AzureDiagnostics
- Playbooks run by Autoamtion Rules – SentinelHealth
- Autoamtion per Incident – SentinelHealth
- Playbooks Billable Info – Azure Resource Graph, not relying on Microsoft Sentinel tables
Let’s take a quick look at the workbook and you’ll quickly see why I love this workbook for trouble-shooting and governance:
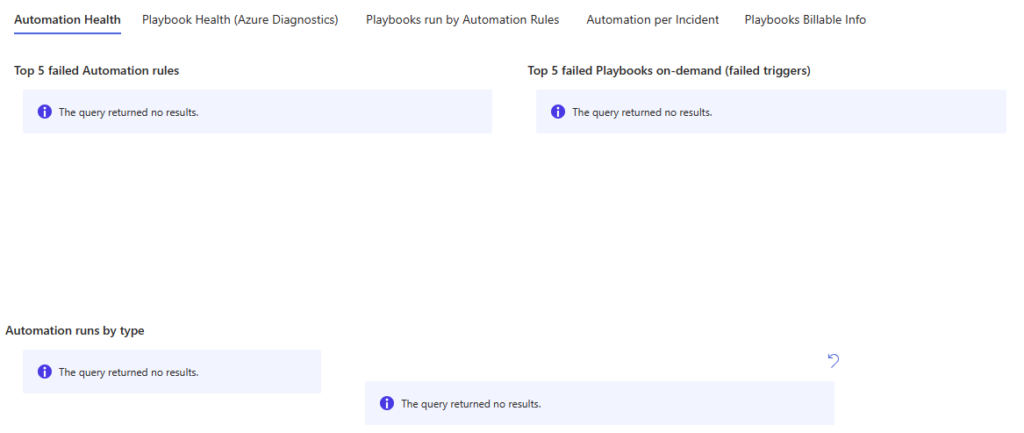
We can easily and quickly see ANY failed automations running in our Sentinel instance. This is a huge time-saver and let’s me focus just on the problems that need to be solved without sifting through any data! Note that beautiful and empty ‘no results’ page!
In the workbook Automation Health, my favourite section is the “Playbooks Billable Info” tab. This shows me the playbooks used with Sentinel, how may runs in the time-period being examined, and associated costs with those runs:
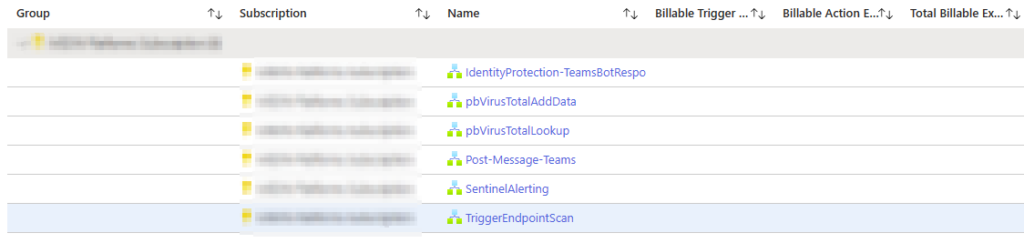
This can really help to understand what automations are costing more than expected, and let’s me quickly spot which playbooks are no longer needed in the environment. If a playbook is not running regularly – ask some questions around it’s intended purpose and usage; we do have playbooks written for incident response that in a perfect world would never run!
Review Access to Sentinel
It is also good practice to review permissions for your Sentinel users. SOC / SecOps / or other team….we still need to do good housekeeping in our own Sentinel ‘house’. Consider how your team is utilizing the built-in roles for Sentinel and if there is room for improvement in the area of least-privilege. In security, we all strive to lead by example, in my experience.
Microsoft Learn does an excellent job of explaining the roles for us (source):
All Microsoft Sentinel built-in roles grant read access to the data in your Microsoft Sentinel workspace.
- Microsoft Sentinel Reader can view data, incidents, workbooks, and other Microsoft Sentinel resources.
- Microsoft Sentinel Responder can, in addition to the above, manage incidents (assign, dismiss, etc.).
- Microsoft Sentinel Contributor can, in addition to the above, install and update solutions from content hub, create and edit workbooks, analytics rules, and other Microsoft Sentinel resources.
- Microsoft Sentinel Playbook Operator can list, view, and manually run playbooks.
- Microsoft Sentinel Automation Contributor allows Microsoft Sentinel to add playbooks to automation rules. It isn’t meant for user accounts.
Next Steps
Some additional take-aways for Sentinel governance to help your SOC team and organization improve together are:
Form a Plan Committee: Establish a committee to oversee the governance of Sentinel. This committee should be responsible for reviewing and approving policies, procedures, and guidelines related to Sentinel.
Regular SOC Activities: Schedule regular SOC activities to ensure continued security best practices. These activities include triaging and investigating incidents, exploring hunting queries and bookmarks, and reviewing and enabling new analytics rules as applicable. Using a schedule for your SOC team can really help ensure that everyone gets a chance to work on tasks that they enjoy!
Integrate with Microsoft Security Services: Integrate Sentinel with other Microsoft security services such as Microsoft Defender for Cloud, Azure Security Center, Defender 365, Endpoint security, and other services in use to enhance the organizational security posture.
Protecting MSSP Intellectual Property: If you are a Managed Security Service Provider (MSSP), ensure that you protect your intellectual property by using a separate Sentinel workspace for each customer. Stay tuned to AzureTracks.com blog for some upcoming Azure Lighthouse discussions!
Threat Intelligence Integration: Integrate Sentinel with threat intelligence feeds to enhance your threat detection capabilities and provide a more holistic analysis on your logs.
Microsoft Sentinel Content and Solutions: Regularly review and update your Sentinel content and solutions to ensure that they are up-to-date and aligned with your organization’s security policies and procedures. This one is a quick and very easy way to keep your connectors and queries updated.
Although this mini-series of articles on Sentinel Governance has been fairly detailed, it is not an exhaustive list of everything that should be done in all circumstances and conditions. Please use your powerful human critical thinking abilities to determine which tasks are appropriate for your environments!
Thank you for following AzureTracks articles & posts! I hope that this little series can help you and your team move forward and really get the most out of your Microsoft Sentinel and tooling!
Source: https://learn.microsoft.com/en-us/azure/sentinel/best-practices