Responding to Incidents with Microsoft Sentinel – Part 5 – Take Action with Automation
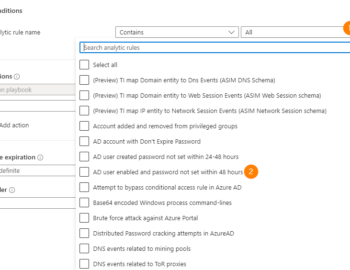
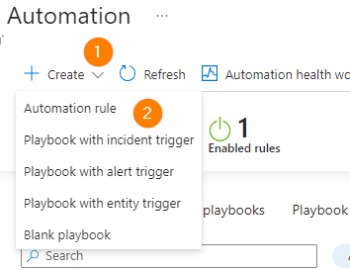
In today’s article we will build on previous automation experiences to further develop your Microsoft Sentinel automation powers! Today we will look at remediating incidents and alerts automatically. We will explore auto-remediation using both playbooks and Sentinel Automation rules.