Sentinel Health Data Visualization & Reporting
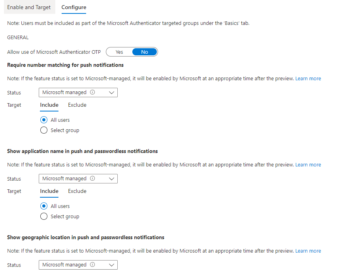
A common challenge after deploying Microsoft Sentinel has been how to keep track of your Data Connector health status. Last article, we explored getting a handle on our Microsoft Sentinel data connectors health. This week, we look visualizing and using that data with Sentinel Workbooks.