
M365 Operating Guide for Sec Ops Teams – Use with Microsoft Sentinel
When building out a SOC team, many organizations quickly realize that there are very few silos left in IT when it comes to cloud. Our SOC members need to have cloud platform skills, M365, Exchange, Active Directory, Azure Active Directory, Windows Server, REHL, and so many more skills. To say this a different way; our cloud landscape is flat, and we need members that have a wide band of skills with some specialties mixed in. This is complex to say the least, and with labour challenges in our post-covid world, we need ways to upskill our teams and build out operations manuals and tasks to support those teams.
Enter the M365 Operating Guide for Sec Ops Teams. Here, Microsoft has provided a high quality and robust approach to protect – detect – and respond to M365 related threats. We will cover what roles your SOC members may use to access information and perform their duties, take a look at a subset of the important tasks to cover, and then we’ll talk a little bit about making sure you have Microsoft 365 Office Activity data integrated with your Microsoft Sentinel deployment, and some other configuration items that may really help your SOC team level-up! First up is how to access the different Areas in Microsoft 365 and Azure.
What Roles Do I Need?
To grant access to your team members, the following roles and role groups are available in Azure AD:
Applicable Azure AD Roles are:
Centralized roles assign permissions are available as roles and role groups to grant permissions to Defender for Office 365, and all global Microsoft 365 Services. You can view all available roles here.
- Security Administrator
- Security Operator
- Security Reader
Email & Collaboration Roles:
- The Preview role is assigned only to the following role groups:
- Data Investigator
- eDiscovery Manager
Search & Purge role:
- This role is needed to approve deleting a message in quarantine, user mailboxes, etc.
- This role is also needed to be able to take actions on messages while performing threat hunting such as in Threat Explorer.
- This role is assigned by default to the following role groups:
- Data Investigator, and
- Organization Management
Tenant AllowBlockList Manager Role:
- This role is used to manage allow & block entries in the Tenant Allow/Block List in Defender for Office 365, blocking of URLs, blocking files using file hashes, and being able to take action on malicious emails while responding to incidents, alerts, and threat hunting.
- By default, this role is available only to the Security Operator role group, but members of Security Administrators and Organization Management role groups can also perform these management tasks.
Tasks To Complete on a Daily Basis:
- Head to https://security.microsoft.com/incidents-queue and check the following:
- Incident Queue
- Alerts
- Automated Investigation & Response (AIR)
- Prioritize events consistently using the suggested pattern:
- A potentially malicious URL click was detected.
- User restricted from sending email.
- Suspicious email sending patterns detected.
- Email reported by user as malware or phish, and Multiple users reported email as malware or phish.
- Email messages containing malicious file removed after delivery, Email messages containing malicious URL removed after delivery, and Email messages from a campaign removed after delivery.
- Phish delivered due to an ETR override, Phish delivered because a user’s Junk Mail folder is disabled, and Phish delivered due to an IP allow policy
- Malware not zapped because ZAP is disabled and Phish not zapped because ZAP is disabled.
- Review email campaigns at https://security.microsoft.com/campaigns.
Perform Triage first, then investigate and take response actions, resolve the incidents, and then classify incidents.
Completing daily operations for MDO in this pattern will give consistent results follow best practices for SOC roles and responsibilities.
There is additional guidance in the source guide on other daily tasks for submitting false positive and false negative detections.
Tasks To Complete on a Weekly Basis:
- Review the Mailflow status report here.
- Review the Threat protection status report here.
- Review threats in your Threat Analytics dashboard here.
- Review top Targeted Users tab in Threat Explorer here.
- Review malware and phishing campaigns that target your organization here.
This is a good place to start for MDO weekly task guidance. Add tasks and reports that are even more targeted for your users and organization to improve and add to this list.
Tasks to Complete on a Weekly Basis:
- Review of Defender for Office 365 policies. This is a task that will help protect against configuration drift and prevent malicious settings. Use the Configuration Analyzer to support consistent results month over month.
- Review detection overrides in MDO here.
- Review priority account memberships here.
Again, this monthly task list is a place to get the team started and should be added to and evolve over time with the organization and SOC needs.
Additional Guidance:
There will always be on-demand investigations and removal of emails. You can start in the Treat Explorer here and begin your investigations from user requests. Your SOC can expand and improve operations by doing PROACTIVE THREAT HUNTING in both Threat Explorer and Advanced Hunting dashboards.
The full Microsoft Defender for Office SecOps Guide can be found here. Please take the time to review and become familiar with more of the tasks you will find in this excellent Microsoft Guide. Tucked into this guide is some real-life activities that SOC’s typically have to deal with – namely false positives and false negatives. Have a look and check out the detailed advice from SOC experts like you!
Integrating Microsoft Office 365 Activity Data with Microsoft Sentinel:
Occasionally I will run across an organization that has not fully realized their logging potential for Office 365 Activity Data with their SIEM/SOAR solutions — my preference is Microsoft Sentinel — but there are a lot of top quality SIEM solutions out there. Let’s use this opportunity to review our Data Connection settings and ensure that we are getting ALL the data that will be useful for us, and that we are examining that data to take actions on potential threats.
Let’s jump right into our Microsoft Sentinel deployment and take a look:
Browse to http://portal.azure.com and get logged into your environment, then proceed to Microsoft Sentinel and select your Log Analytics workspace. Alright, now let’s jump down to Data Connectors.
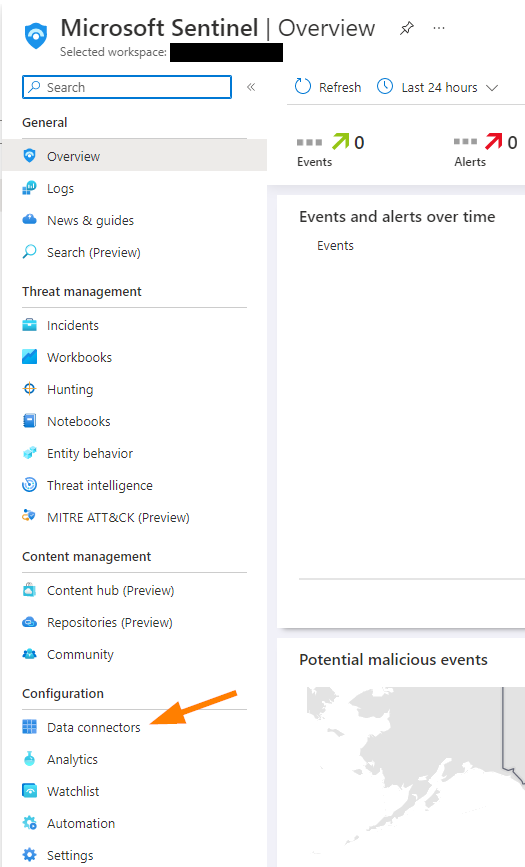
When the blade loads, click into the search field and type “office”.
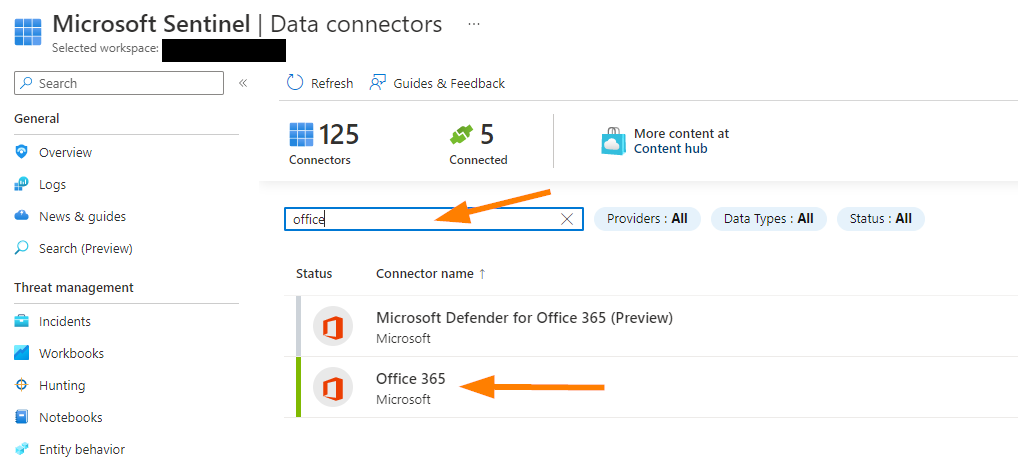
Select your Office 365 Data Connector. Next, click on OPEN CONNECTOR PAGE near the bottom of the pop-up blade.
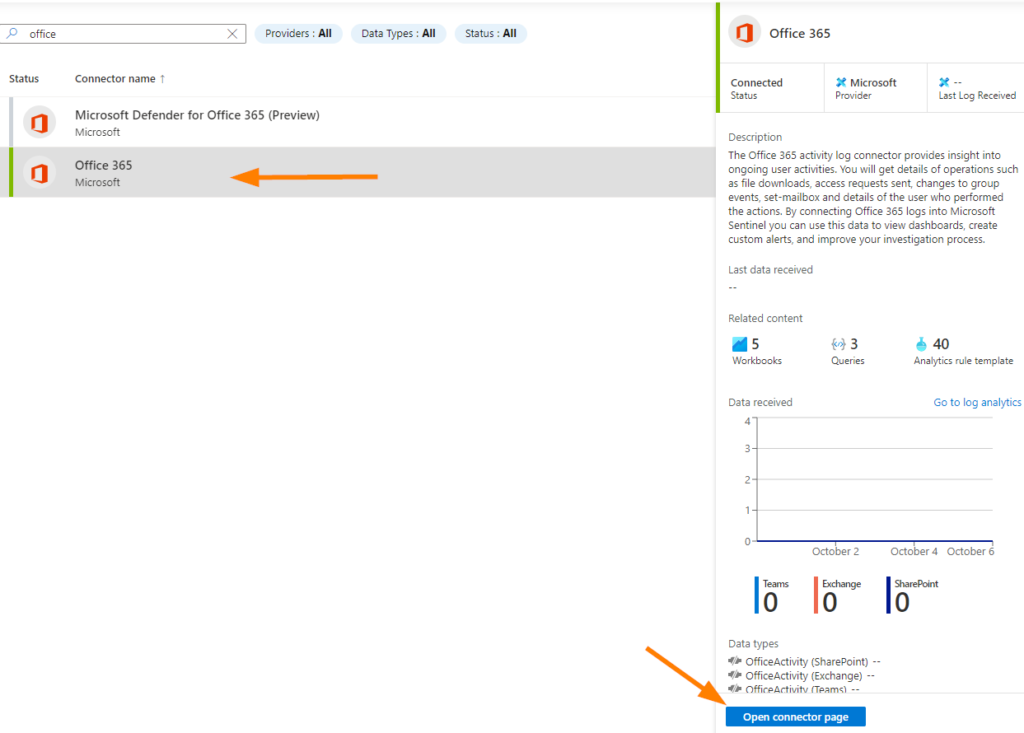
Review your CONFIGURATION section to ensure you have all the record types desired selected. Now, my example is just a little test tenant, so a lot of options are missing, but you should see a bunch of Microsoft 365 services populated in there.
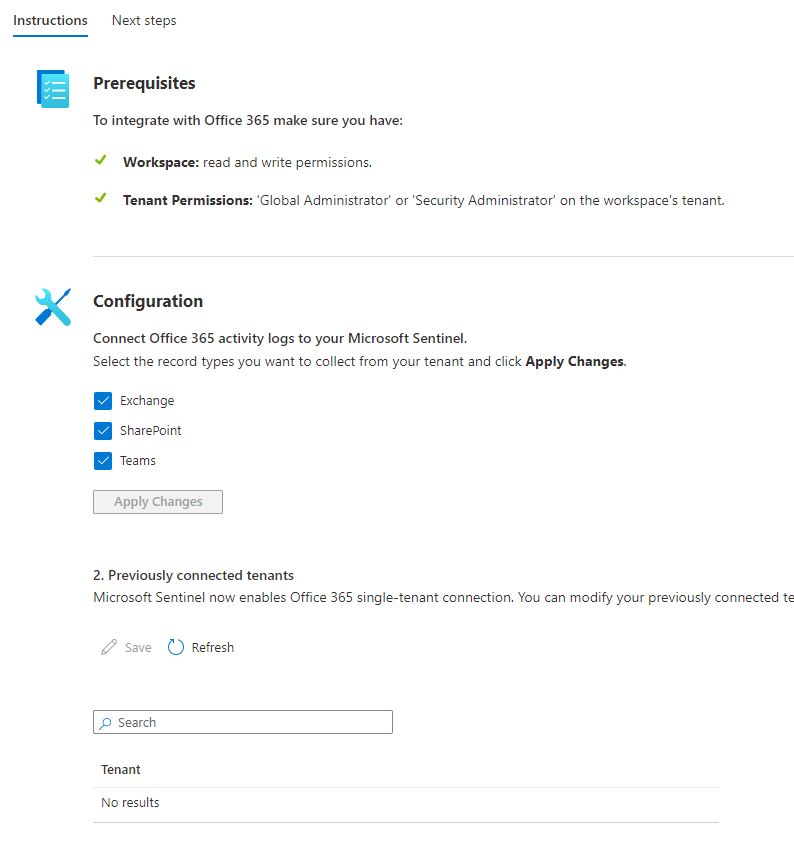
Save any changes by clicking APPLY CHANGES.
Now we’ve checked on those data connector settings, let’s take a quick look at the Analytics rules tied to this data.
Remember that little “40 Analytics Rule Templates” you may have noticed on the data connector pop-up blade?
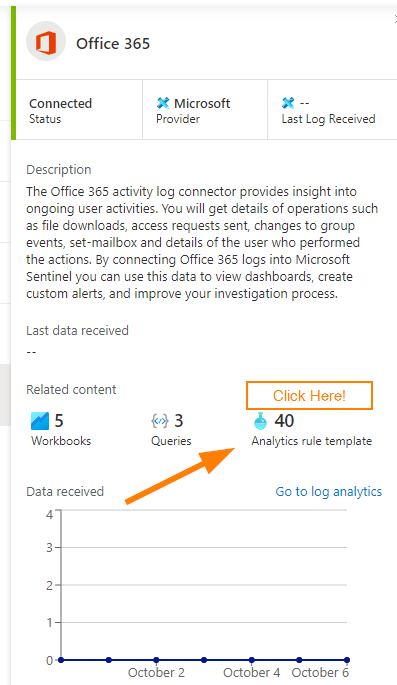
When you click on the 40 (or other number that you may see!), you should see something like this:
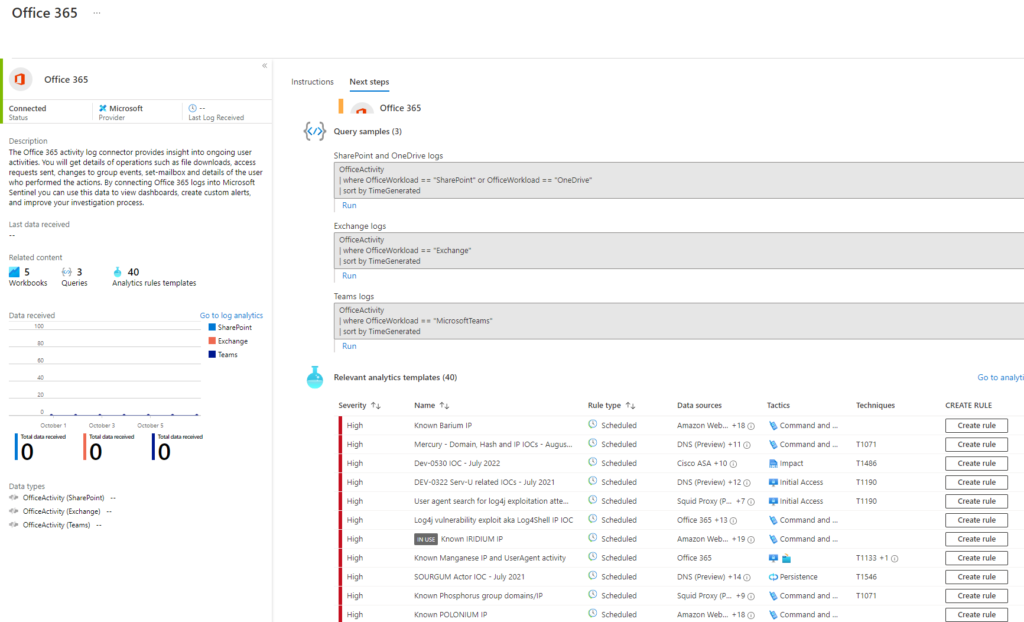
Now, in my case, most of my rules are added or available but not enabled. You can click on CREATE RULE or ENABLE RULE right here.
Also, notice that near the top of this fantastic blade, you will have some recommended WORKBOOKS that you can also add to help you work through your collected data! Just awesome! Go ahead and explore what you’ve been missing here……while you are busy working through detection and alerting rules, I’m going to go to work on my next article!
Thanks for joining me for this very important topic. My hope is that you will get at least one helpful hint from this, and that you do go check the Microsoft source here to get always up-to-date information from Microsoft Learn content.