Modernize your Microsoft Authenticator Policies
Getting ready to move into Azure Active Directory or make changes to your Microsoft Entra configurations? The last few weeks I’ve talked about MFA and conditional access rules; so this week we will look at the preview for Microsoft Authenticator Policies, then change gears and talk about how to get our users excited about these security enhancements.
The Microsoft Authenticator app will start enforcing number match on all Azure AD tenants Feb 27, 2023. We have some time to get ready, but why wait when it’s so easy to get everything planned and rolled out right?
We’ve talked about securing the organization better, improving resistance to phishing, and various configuration improvements for Microsoft Entra. Today, let’s talk about modernizing our Microsoft Authenticator Policies and getting users excited, providing our users the right educational materials, and getting our people ready for the technology changes. This is how we can ensure our rollout is truly successful.
Let’s talk about the Microsoft Authenticator changes for Feb 2023 a little bit. Did you know you can enable them now in your tenant by modernizing your settings in advance? The functionality is currently in Preview, so you can test this out and get ready for production changes coming soon to Azure AD near you!
Check out your Azure AD Portal at https://portal.azure.com/ > Azure Active Directory > Security > Authentication Methods > then choose Microsoft Authenticator.
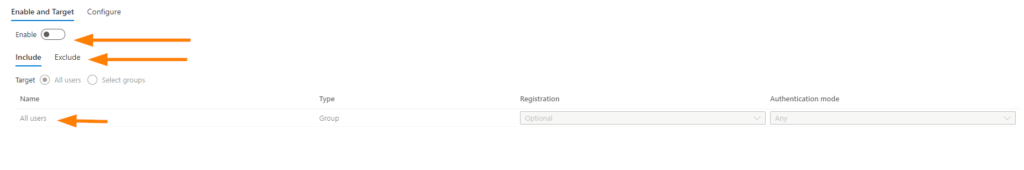
First, enable the policy for Microsoft Authenticator, this is the new area to manage your MFA policies once all changes come into effect in General Availability.
Once your enabled, set your options for which groups to include, and ensure that you exclude your Break Glass account as always for policy configurations in MFA and conditional access. Save the changes and proceed to the Configure blade.

Next, we mix up the order a bit here as users should be registered for Passwordless authentication to fully take advantage of all these awesome enhancements. We’ll talk more about how to get your users on board with these changes shortly. Back to our Microsoft Authenticator settings…
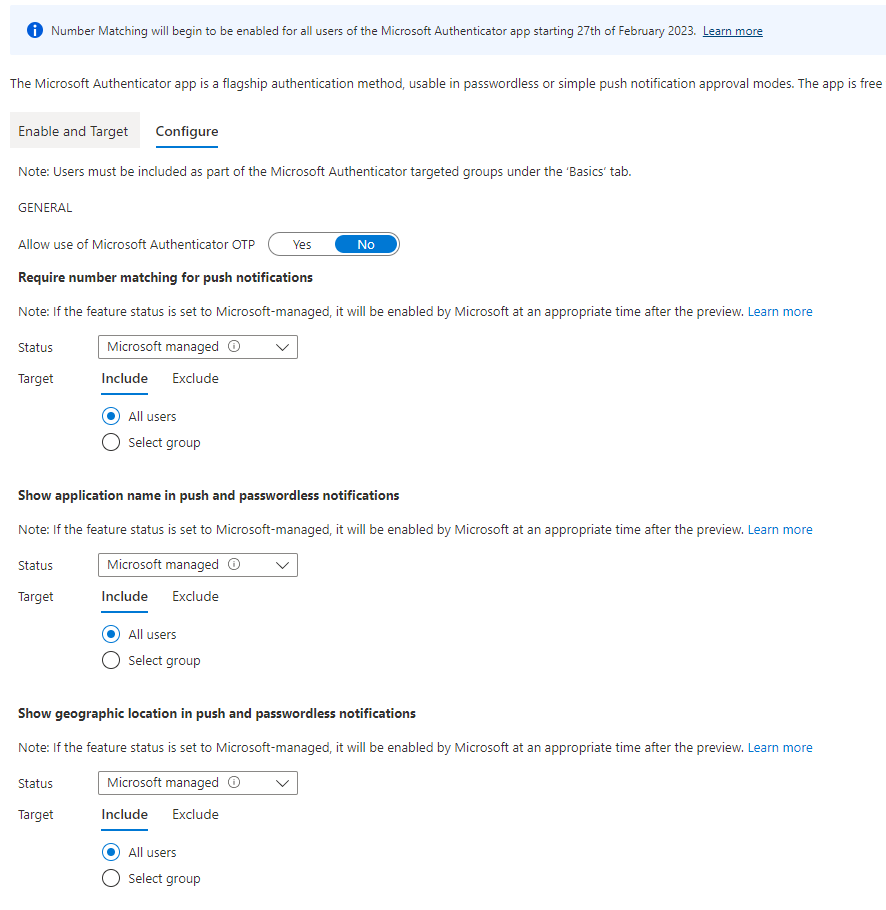
On the Configure Blade, you can select to allow use of Microsoft Authenticator OTP (One Time Passcode) or disable it (default is No = Off) for enhanced security configurations.
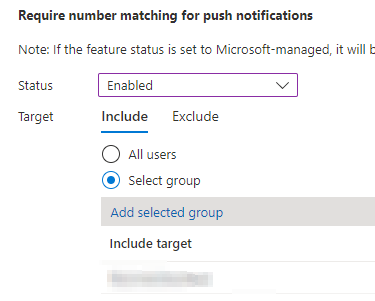
Now the fun setting! Require Number Matching for Push Notifications > set Status to Enabled to turn it on today, and Target your setting to a group. It is recommended to set a Security Group here, and again, exclude your Break Glass account.
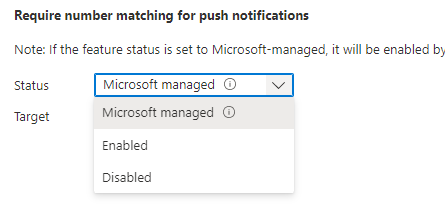
Adjusted settings:
Set the other enhanced features such as Show Application Name and Show Geographic Location. I’m a big fan of Geographic Location because it allows the user to validate the logon is coming from the expected location where they are. This is a great enhanced feature and will support greatly reducing MFA errors and fatigue issues overall.
Next up is how the change will look, and how we get our users to be as excited as we are for these changes!
Microsoft Authenticator will look a lot like this once we make these changes:
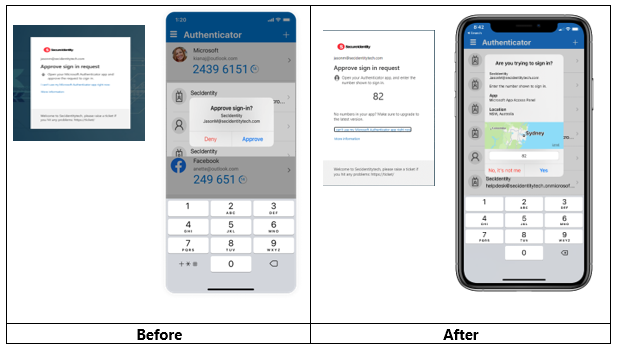
Once you are ready to jump in and start your plan, Microsoft has made some excellent templates available to everyone to support your MFA initiatives. From initial rollout and user on-boarding, helpdesk educational content, user instructions to get registered for SSPR (Self Service Password Reset) and MFA, to Passwordless enablement, or images like you see above to help show what Authenticator will look like with Number Matching and Geographical Location options enabled.
Remember to map out your organization’s path to MFA modernization and plan the changes thoughtfully as I know we all do!
The key items I like to think about as planning an MFA rollout:
- Microsoft Authenticator usage, compatibility, and deployment to mobile devices
- What business requirements do we need to consider for compliance and security?
- Deploy apps to mobiles
- BYOB devices vs company provided
- Are all applications capable of being supported with Microsoft Azure AD / Authenticator?
- SSPR configuration and usage
- MFA Policy – Microsoft Authenticator Policy (Modernized Settings)
- Conditional Access Policy
- Phish resistence
- Location restrictions
- Managed devices (IE: Azure Hybrid Joined)
- Other business requirements and security enhancements
- Logistics and Project Management
- Targeted Scope for rollouts
- POC goals and requirements
- Timing alignment with business blackout periods, holidays, etc.
- User onboarding and support plan
Once you have decided on the deployment configurations, schedules, and associated planning; it will be time to build your user onboarding and support plan along-side. This where we can incorporate the ready to use templates. All of these Microsoft templates for Word, PowerPoint, images, Emails and more can all be branded and updated with your Helpdesk information and logos. This makes a really great and custom approach to educating your users.
Onboarding and adoption of changes is greatly improved with some personalized touches and good documentation! Check out the templates here: https://aka.ms/mfatemplates.
Enjoy testing and checking out the new features and getting ready for the new ways we can enhance our Azure AD identity security with a full view from business requirements to users.