Advanced Customization of Microsoft Sentinel Analytics Rules
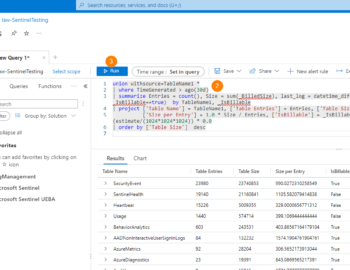
Join me as we walk through creating a custom Microsoft Sentinel Analytics Rule using KQL to identify suspicious login patterns based on failed attempts. We will explore the different components of creating these custom rules, what tuning looks like, and creating incidents from the rules.