Responding to Incidents in Microsoft Sentinel
In this article we will explore next steps once you have investigated an incident. Taking action to respond to the threat. Microsoft Sentinel provides excellent automated response capabilities that can be used to respond to threats in real-time.
For example, you can quarantine an infected device or block a suspicious IP address. You can also create custom workflows that automate the incident response process.
Today, we will build on our last article and discuss the foundations of responding to incidents with Microsoft Sentinel; sprinkling in the discussions of automation along the way. As I write this article, the world excitedly awaits Microsoft Security Co-Pilot announcements, so the way we respond to incidents will definitely change as those solid AI capabilities come into our production systems. Let’s start our exploration of incident response here…
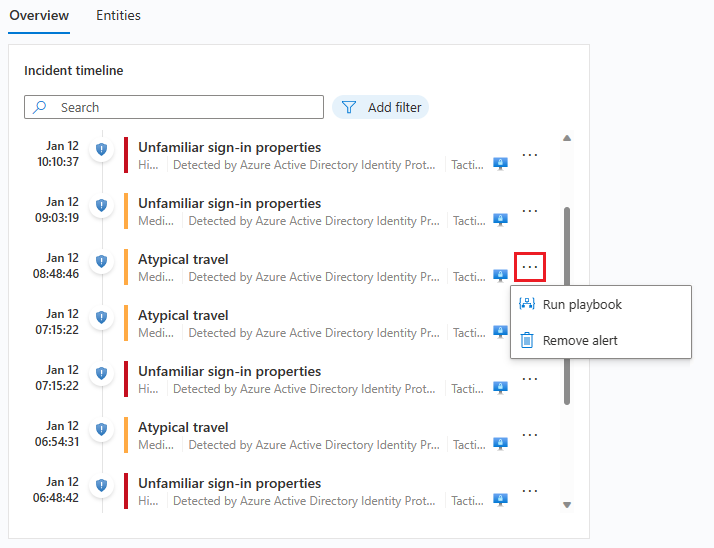
Responding to Incidents is a critical part of the incident management process in Microsoft Sentinel. You would use the information you’ve gathered during an investigation to take action and mitigate the threat.
Here are some of the ways you can respond to incidents in Microsoft Sentinel:
- Automated response: Microsoft Sentinel includes a number of automated response capabilities that allow you to respond to incidents in real-time. For example, you can use playbooks to automatically isolate a compromised device or block an IP address. These automated responses can help contain the threat and prevent further damage. As shown above in the screenshot, you can run a playbook right from the Incident Timeline and isolate and endpoint to allow your team time to investigate further AND isolate to stop the spread of malware threats. Some additional tools to automate incident response include:
- Azure Security Center: Azure Security Center is a cloud-native security solution that provides advanced threat protection across your hybrid cloud workloads. It includes built-in security policies and recommendations, as well as automated responses to security threats. As an example, you can configure Security Center to automatically quarantine a virtual machine if it’s found to be compromised.
- Azure Automation: Azure Automation is a cloud-based automation service that allows you to automate common tasks across your Azure resources. You can use it to create runbooks, which are collections of automated tasks that can be triggered by a specific event or schedule. For example, you can create a runbook that automatically disables a compromised user account.
- This automation tool allows us to use PowerShell, and other languages or tools, so that you can even recycle some traditional or previously created scripts. Just saying that this options gets used a lot by a certain author.
- Azure Logic Apps: Azure Logic Apps is a cloud-based service that allows you to create workflows and automate business processes. You can use it to create automated responses to security incidents, such as sending an email notification or creating a ticket in a helpdesk system.
- Logic Apps are a great way to integrate with 3rd party ticketing systems that you need to get a notification submitted to. This is especially helpful for 24hour alerting if your security team is not 24hour.
- Microsoft Power Automate: Microsoft Power Automate (formerly known as Microsoft Flow) is a cloud-based service that allows you to create workflows and automate tasks across multiple applications and services. You can use it to automate responses to security incidents, such as sending an alert to a Microsoft Teams channel or creating a new record in a customer relationship management (CRM) system.
- Microsoft 365 Defender: Microsoft 365 Defender is a cloud-based suite of security tools that provides advanced threat protection for your Microsoft 365 environment. It includes automated responses to security threats, such as quarantining a malicious email or blocking a malicious file from being downloaded.
- Manual response: In some cases, you may need to take manual action to respond to an incident. For example, you may need to disable a compromised user account or remove malware from a device. Microsoft Sentinel provides detailed information about the incident, including the affected assets and the type of threat, which can help you determine the appropriate response.
- Collaboration: Microsoft Sentinel provides collaboration features that allow you to work with other members of your team to respond to an incident. As an example, you can assign tasks to team members or share information about the incident in real-time. This collaboration can help ensure a coordinated response and improve the speed and effectiveness of your incident management. Another great example of collaboration with incident management is taking advantage of the Microsoft Teams solution in Sentinel — this allows your team to work together in a Teams channel on major incidents to speed response and improve outcomes by working together. I have found this to be an excellent way to work with remote team members together and bridge that gap. We have the tools available, let’s use them!
- Reporting: After you’ve responded to an incident, it’s important to document your actions and provide a report to management. Microsoft Sentinel includes reporting features that allow you to generate reports on incidents, including the actions taken, the outcomes, and any lessons learned. These reports can help you improve your incident management process over time.
- Continuous improvement: Finally, it’s important to use the information you’ve gathered during the incident management process to continuously improve your security posture. Microsoft Sentinel provides analytics and reporting features that allow you to identify trends and patterns in your security data. By analyzing this data, you can identify areas of weakness and implement measures to improve your security over time. This is a whole topic on it’s own, but it is important to keep it highlighted. Also, remember to re-visit data connectors, any data filtering or exclusions in place, analytics rules, automation rules, and playbooks to make small improvements on a regular basis.
Conclusion
Overall, responding to incidents in Microsoft Sentinel involves a combination of automated and manual responses, collaboration with your team, and continuous improvement of your incident management process. By using these features effectively, you can minimize the impact of security incidents and improve the security posture of your organization.
Working together as a team, hearing all the suggestions to improve automation, and good old-fashioned cooperation, will really support a healthy security team environment that encourages a natural growth. You may just find that team members will encourage each other to learn new things, push boundaries, and in doing so…improve your organization by leading.
I’ll be publishing a mini-series on some of my favourite configurations to help optimize what we pay attention to in our Microsoft Sentinel queue. I’ll explore automations, and some additional optimizing that can save time for everyone working in Sentinel.