
Ready to modernize your MFA?
Using multifactor authentication (MFA) is how organizations help prevent unauthorized access to applications and data. Simply turning on MFA and grabbing a coffee won’t cut it; the truth is, that hasn’t supported improved security measures for quite some time. Let’s take a look at how we can modernize our MFA and move closer towards zero-trust.
There is a lot of guidance on what MFA can and cannot do to help us. Let’s talk briefly about the basics. We will be addressing Azure Active Directory as our identity management system in this article.
When we first start a multifactor authentication journey, we usually enable some foundational methods such as Microsoft Authenticator, phone call, text message, and sometimes a security key (USB security key). These are great to get started, and even a few years ago, put an organization ahead in terms of protection against phishing sites and credential theft.
Today, we need to improve our position. It’s time to modernize our MFA. Let’s acknowledge that Federated Identity systems like AD FS, although great for many reasons, are now generally accepted as a legacy method of authentication. I know, it’s been hovering around for a few years on the edge, but it’s time to consider that our complex AD FS systems can be modernized. Ask your favorite Microsoft Partner or Rep to help you assess your AD FS and find a path to migrate managed applications to Azure AD and modern methods all-around. There are options, and it’s not as tough as you may think! Alright, let’s move ahead.
Next up is our good friend – the Microsoft Authenticator App. When deployed ‘vanilla’ without any additional supports such as conditional access policies, it adds a layer of -basic- protection. This is what many organizations are still running in production today, and one of the biggest root causes of credential compromise that I see with different organizations. Working with SOC and Support teams to prevent some common challenges around authentication compromise has a few common themes:
- A personal computer or tablet can login to company resources the same way as a company computer or tablet,
- Employees were last trained – either never – or very infrequently, and
- Password policy has not been modernized and requires some overly complex structures.
Let’s move forward into modernization together!
Now that we understand some of the challenges, and how just having MFA alone doesn’t help as much we all would like; let’s look at modernizing our position and helping to secure our applications, data, and users. As a bit of a note here, if your organization is NOT using MFA today, plan your change and turn it on today. It’s easy, and Azure Active Directory supports most basic scenarios to get you started. It’s important, and it’s 2022 Q4 on my calendar….let’s just get it done!
Ok, now that we’ve cleared the air — let’s move right into what we can do to Modernize our MFA!
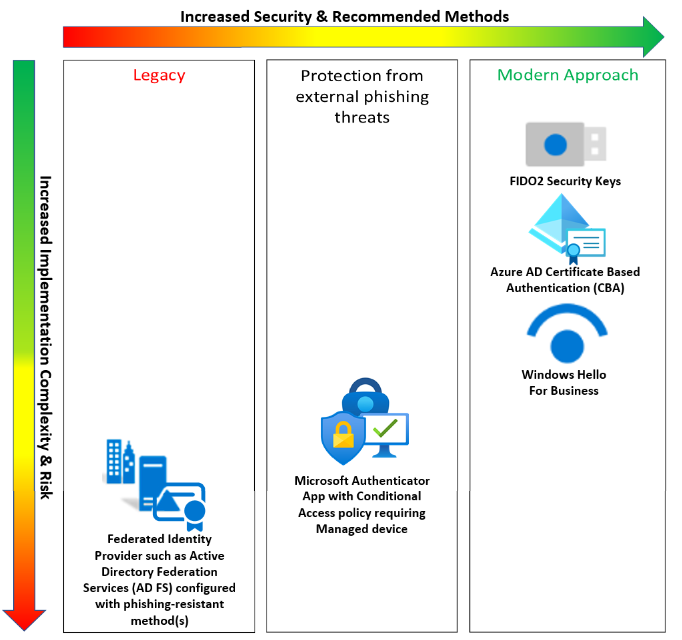
First up is how to meet the phishing-resistant protection from external threats:
1. Use Microsoft Authenticator with conditional access policies to ensure managed devices are being authenticated and that the device is marked as compliant.
- The device accessing your application or data should be managed
- All users that are able to use Microsoft Authenticator must also be included in a conditional access policy that requires a managed device for access to all applications
- There also needs to be a conditional access policy that blocks access targeting the Microsoft InTune Enrollment Cloud App. All users allowed to use Microsoft Authenticator must also be in scope for this conditional access policy.
To accomplish this, use a single group to scope users for both conditional access policies mentioned above. This prevents the most common threats of unmanaged devices accessing systems and preventing a compromised account from registering a device through InTune.
2. Train the people.
Work with your Corporate Trainer, Organizational Change Management team, or find your favourite partner to support your organization through Cyber Security Training. There are amazing options around that require low-effort to organize with huge benefits. This is the training that I really enjoy seeing rolled out as people take these improved or new skills home with them and help more people protect themselves. This is also available as part of Microsoft 365 Defender for Office Plan 2 license as Attack Simulator Training, you test and train your people right through your M365 portal. If you have roll-up licenses such as E5 flavours, you may already have this license, so go check it out.
3. Password complexity.
This final item is still a topic that many professionals and administrators hold on to legacy thinking with. It’s a tough topic in many rooms. To get ready for zero-trust, and modernize an organization’s position, password policies should not require the use of special characters or regular rotation.
I don’t think I need to say it…but many, many organizations are still stuck on this one. I would encourage those organizations to look to current NIST standards, Microsoft Security guidance, and explore the modern authentication standards that help contribute towards zero-trust. I really do want all of us to move this forwards and be ready to meet the requirements for zero-trust and a modern approach to authentication.
The Modern Approach
To truly modernize our authentication and move towards zero-trust, we need to look at the following:
- FIDO2 security keys. Whether it be USB-C or more, FIDO2 security keys are the accepted gold standard of MFA.
- Azure AD Certificate-based authentication. AAD certificate based authentication removes the dependency of a federated identity provider and includes other authentication tools such as smart cards and derived PIV credentials that are deployed to mobile devices or security keys.
- Windows Hello for Business. This passwordless MFA authentication that is phishing-resistant improves usability for many of our people that may not embrace a USB security key.
To get the modern authentication benefits, remember to build the layers of conditional access policies with the foundational steps. Here are a couple of additional resources to help plan the deployments for moving forward.
Devices need to be either Azure AD or Hybrid joined: https://learn.microsoft.com/en-us/azure/active-directory/devices/hybrid-azuread-join-plan
Require a compliant device that is hybrid Azure AD joined: https://learn.microsoft.com/en-us/azure/active-directory/conditional-access/howto-conditional-access-policy-compliant-device
While moving authentication methods ahead has traditionally been fairly complex, Microsoft has done some incredible work to make these moves much easier. I have been a fan of Microsoft Authenticator App for a long time, and utilizing supporting technologies such as well designed Conditional Access policies, will really help to enhance any identity management system in place today. Let’s all do our part to improve identity security and reduce credential theft.
Thanks for joining me for this long-overdue discussion on multifactor authentication and modernization. If you would like to know more about identity security, check out Microsoft Learn at https://learn.microsoft.com and check out the great documentation on MFA, conditional access, and all things identity.
Sources:
https://learn.microsoft.com/en-us/azure/active-directory/standards/memo-22-09-multi-factor-authentication
https://learn.microsoft.com/en-us/azure/active-directory/standards/memo-22-09-meet-identity-requirements