
Responding to Incidents with Microsoft Sentinel – Part 3 – Gather Research Automatically
In this article we will explore automation enhancements to your Microsoft Sentinel environment. Today we will take a look at using Sentinel Playbooks and gathering information on an Incident automatically. If you missed it, the previous article is here. Let’s look at using Sentinel Playbook automation to do some research automatically before we ever put eyes on our incidents.
One way to build automation in Microsoft Sentinel is Playbook Automation, which allows security Analysts to automate repetitive and time-consuming tasks, enabling them to focus on critical aspects of incident response. In this article, we will explore an example of using Playbook Automation in Microsoft Sentinel to perform information lookup during an incident investigation.
This is a key step that can be done before a SOC Analyst ever opens an Incident to work on. Having as much research and other lookups done before the Analyst works on the incident is a powerful way to optimize time management, and do repetitive tasks ahead of time.
Scenario:
Let’s consider a hypothetical scenario where your organization’s security operations center (SOC) receives an alert regarding suspicious network activity on a server. The alert indicates a potential compromise and warrants immediate investigation. As a security analyst, you want to quickly gather relevant information about the server, such as its owner, last known activity, and associated IP addresses. By leveraging Playbook Automation in Microsoft Sentinel, you can streamline this process and expedite your investigation.
Step 1: Creating the Playbook:
To begin, head to Azure Portal at https://portal.azure.com, then log in to your Microsoft Sentinel console and navigate to the Automation section. Click on “Create Playbook with Incident Trigger” to start building your playbook.
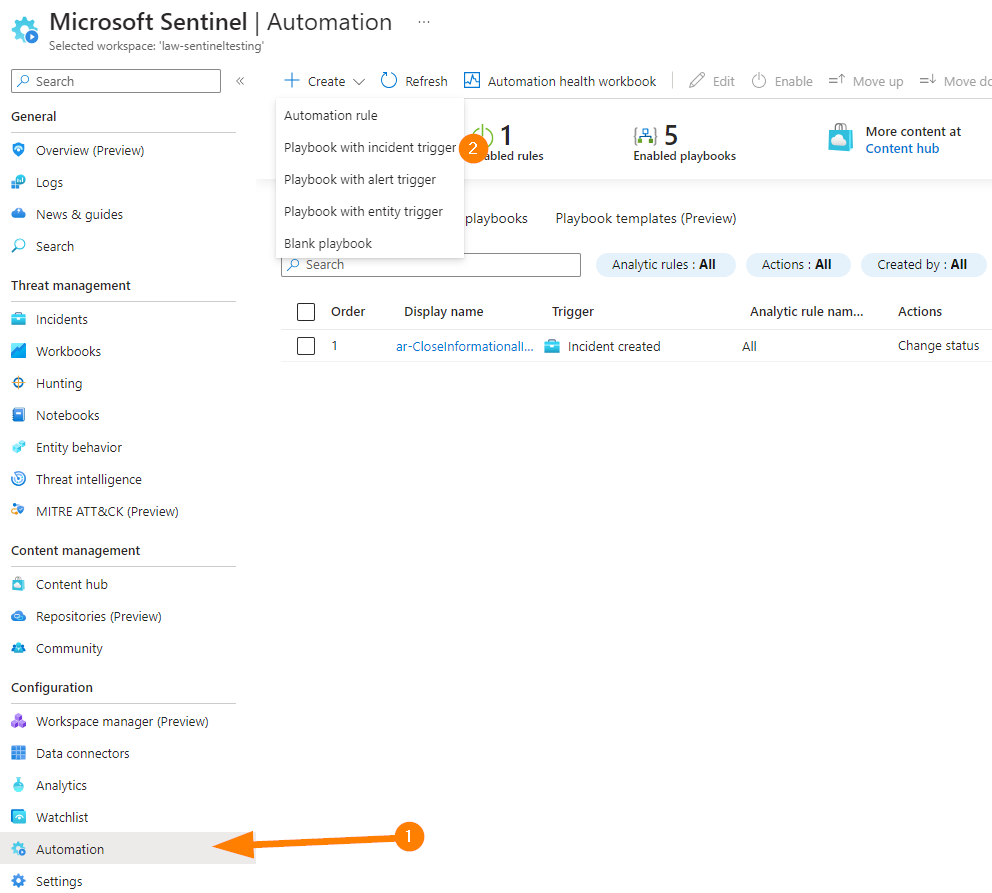
Next, fill out the name and other required fields. Then proceed through the other tabs:
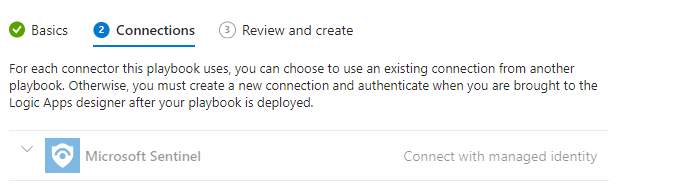
Notice that we get a managed identity built in! No additional connections are required at this step.
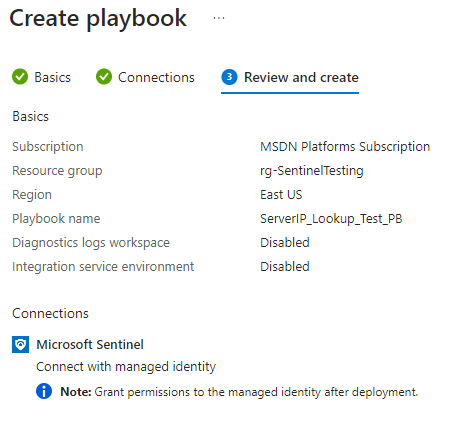
Click on CREATE AN CONTINUE TO DESIGNER
You should now see the Logic App Designer screen:

Step 2: Defining Inputs:
In the Playbook Designer, define the necessary inputs for your playbook. For our scenario, we need an input for the server’s IP address. Add a Sentinel GET IPs (Preview) step and add the Dynamic field ENTITIES.
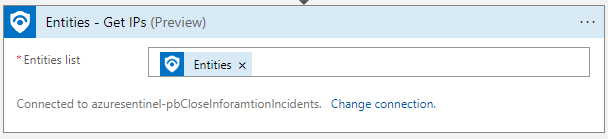
Step 3: Adding Playbook Actions:
Next, add the required playbook actions to retrieve the desired information about the server. In this example, we will use the following actions:
a. Azure Log Analytics Query: Use this action to query the Azure Log Analytics workspace for details about the server based on its IP address.
b. Microsoft Graph Security API: Utilize this action to fetch additional contextual information about the server, such as its owner and last known activity.
Step 4: Configuring Playbook Actions:
Configure each playbook action by providing the necessary inputs and parameters. For the Azure Log Analytics Query action, write a query to retrieve the relevant server details. For the Microsoft Graph Security API action, specify the required permissions and scope to access the server information.
Step 5: Handling Outputs:
After executing the playbook actions, you need to capture the output and make it available for further analysis or use. Create output variables to store the retrieved server details, such as “ServerOwner” and “LastActivityTime” or other tags and values that can be returned from resources.
Step 6: Testing and Refining:
Once you have configured the playbook, it’s essential to test its functionality and make any necessary refinements. Simulate an incident by providing a sample server IP address and verify if the playbook successfully retrieves the desired information.
Step 7: Integration with Incidents:
To further automate the incident response process, integrate the playbook with the incident creation workflow in Microsoft Sentinel. This integration ensures that the playbook is triggered automatically whenever a relevant alert is generated.
Conclusion:
By leveraging Playbook Automation in Microsoft Sentinel, Analysts can significantly enhance their incident response capabilities. In this example, we demonstrated how to create a playbook that retrieves information about a server during an investigation. This streamlined approach reduces manual effort, expedites the incident response process, and empowers analysts to make well-informed decisions quickly. With Microsoft Sentinel’s Playbook Automation, organizations can efficiently respond to security incidents, strengthen their defenses, and safeguard their digital assets by using Azure native automation tools to do the research before we even open the incident.