
Where to find Incident Investigation Artifacts in M365
A common challenge that security teams face is simply not knowing where all the artifacts can be found during an investigation. Microsoft Defender tools are capable of collecting a lot of data, and that can create questions during investigations of where is all this data and how do I find it quickly? Join me for a tour of the basics of Defender data retention periods and where to find that data. Let’s jump right in…
Security team members often ask about where they can find data relating to a particular type of incident, such as a Defender for Endpoint or Phishing email. When gathering that data, the next question is often “How long is this data retained?”.
There are some different retention periods for M365 and Defender of all the things data types. Let’s take a moment to understand the basics.
First let’s make sure we all know about Immutable, meaning that the storage or data is unable to be changed. You may have heard this referred to as WORM or write once read many storage. It’s an excellent system to use for log retention of critical security logs (and other data types of course), as the data cannot be deleted or altered after it is written.
Translator table:
MDE = Microsoft Defender for Endpoint
MDO = Microsoft Defender for Office 365
MDI = Microsoft Defender for Identity
| Endpoint | Microsoft Cloud | |
| Data Immutability | Can be tampered with | Cannot be tampered with |
| Data Availability & Retention | Primarily configuration based | Primarily license based –MDE Plan 1 & 2 – Set in Portal up to 180 days –MDE Advanced Hunting threat-hunting tool allows exploring 30 days of raw data –MDO Plan 1 – 7 days of Alert audit logs and 10 to 90 days for other data types (See Here) –MDO Plan 2 – 30 days of Alert audit logs and 30 to 180 days for other data types (See Here) –MDI is now integrated into the Defender Security data (Think Microsoft 365 Defender Portal > We’ll see this one later on.) and default retention is 90 days. Further – Office 365 Unified Log stores data for the following retention periods by license: -30 days by default or with business tier -90 days with Enterprise E3 -1 year with Enterprise E5 |
| Other Retention Options | Must be local or reachable to each endpoint | Log Analytics Workspace -Easily configured for custom retention of logs -Save data in one spot for up to 7 years -Use RBAC (Role Based Access Control) and Azure AD to help control access and restrict ability to access logs |
Log Data Types Available & Interconnectivity
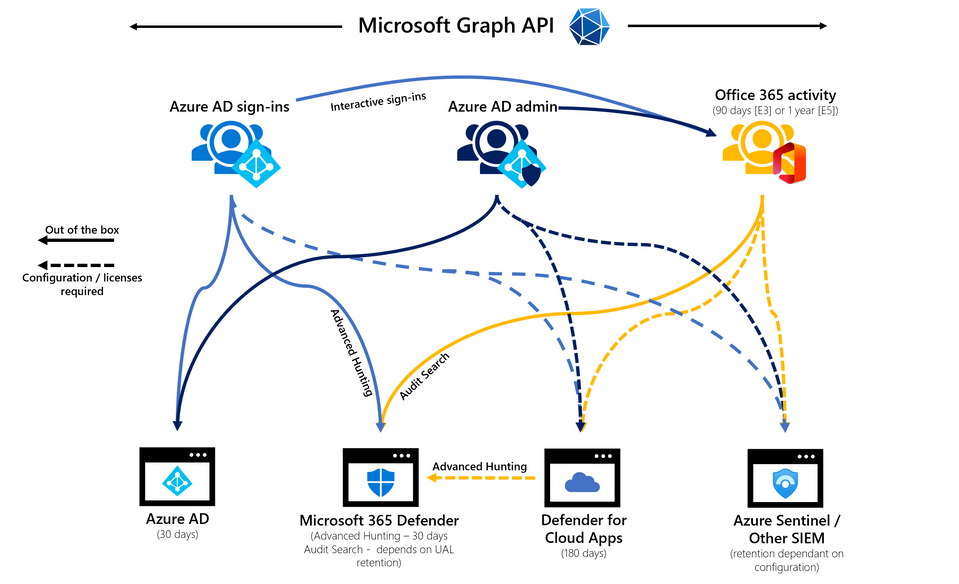
There are a lot of types of log data in the Microsoft 365 eco-system. Let’s start breaking down what data is where, then we’ll take a look at the 3 most likely portals that you will use to work with this data.
What Data is in What Log?
Azure AD Sign-ins
Interactive sign-ins flow automatically to Azure AD and Microsoft 365 Defender to the Office 365 Unified Audit Log. There are a number of other scenarios where you can add destinations to this data flow:
- Enable integration with Microsoft Defender for Cloud Apps through the Office 365 Activity connector.
- Integrate with Log Analytics in your Azure tenant. This is an optimal expansion as you can define longer data retention, use KQL to report on and visualize your data which is all done without the use of a SIEM/SOAR solution.
- Enable integration into Microsoft Sentinel with a data connector. This is my favourite option so that we can use the sign-in data and correlate it with other sources efficiently.
- Integration with any other solution can be done through Event Hubs in Azure as well. This allows the sign-in data to be used in any solution.
Identity is the security perimeter and the associated data is part of a thorough and successful investigation. Finding malicious sign-in activity helps us to understand which Microsoft 365 services require further investigation and where we should focus our attention. There are four categories of sign-ins:
| Interactive | Non-interactive | Service Principal | Managed Identities |
| Sign-ins where a user provides an authentication factor, such as a password, a response through an MFA app, a biometric factor, or some other method. | Sign-ins performed by a client on behalf of a user. These sign-ins don’t require any interaction or authentication factor from the user. | Sign-ins by apps and service principals that do not involve any user. In these sign-ins, the app or service provides a credential on its own behalf to authenticate or access resources. | Sign-ins by Azure resources that have secrets managed by Azure. |
Azure AD Admin Activity
Azure Active Directory (AAD) activity is stored in the Azure AD Audit Log for 30 days and flows to the Office 365 Unified Audit Log. Take a quick look back up earlier in this article where I’ve listed out the retention period defaults for the Office 365 Unified Audit Log.
Retention is 30 days for lower tier licenses, 90 days for E3, and 1 year for E5/F5/A5/G5 licenses or an appropriate add-on for compliance.
The Office 365 Unified Audit log is a critical source for overall auditing and incident investigation. This log includes the following:
- Policy changes including new or deleted policies
- User / Group / Device changes
- Application changes
- Authentication method changes
- Administrative role changes
- Hybrid authentication changes
- This also includes logged changes from Azure AD Connect synchronization status and federation changes.
Office 365 Activity
This log represents another critical data source for our investigations. This data is stored in the Unified Audit Log and incudes the following:
- Unified Audit Log data is retained for 90 days by default or longer if customers have the E5/F5/A5/G5 licenses or an appropriate add-on for compliance.
- You can access data using Audit Search in M365 Defender and can filter on limited fields.
- You can also access this data using PowerShell with the Search-UnifiedAuditLog cmdlet. There are more options to filter using the cmdlet, though results are limited to 5000.
- Data for all Microsoft 365 workloads can be found in the UAL.
- Common workloads for investigation are:
- Exchange Online
- SharePoint Online
- Teams
- Power Automate
- Flow
- eDiscovery
The Portals
Curious where you can find all these portals quickly? Join me for Part 2 of this article for a summary of the top 3 portals and some awesome bonus content on finding other portals in the Microsoft eco-system!
Source:
https://techcommunity.microsoft.com/t5/security-compliance-and-identity/forensic-artifacts-in-office-365-and-where-to-find-them/ba-p/3634865