
Detecting Common Email Inbox Rule Manipulation
In today’s digital landscape, email remains a primary vector for data exfiltration and cyberattacks. With the increasing sophistication of threats, it’s crucial for organizations to have robust mechanisms in place to detect and respond to unusual email activities. Microsoft Sentinel, with its powerful threat detection capabilities, provides the perfect platform for monitoring and securing your email communications.
This article dives deep into the world of Kusto Query Language (KQL) to show you how to create custom analytics rules for detecting high-volume email sends, both internal and external, that might indicate potential security breaches. By leveraging these KQL queries, you can gain valuable insights into your email traffic, identify suspicious patterns, and take proactive measures to safeguard your organization’s data.
Join us as we explore detailed KQL examples and best practices to enhance your email security posture with Microsoft Sentinel. Whether you’re an experienced security analyst or just getting started with Sentinel, this guide will equip you with the tools you need to stay ahead of the curve.
Let’s dive in!
In the most recent Digital Defense Report from Microsoft, business email compromise has been identified as one of the more common attack vectors –still– and we can take some steps in Sentinel to help drive early detection when unauthorized access to email accounts is happening.
There are some basic detections we can do to help drive this early detection when it comes to finding malicious inbox rules in particular.
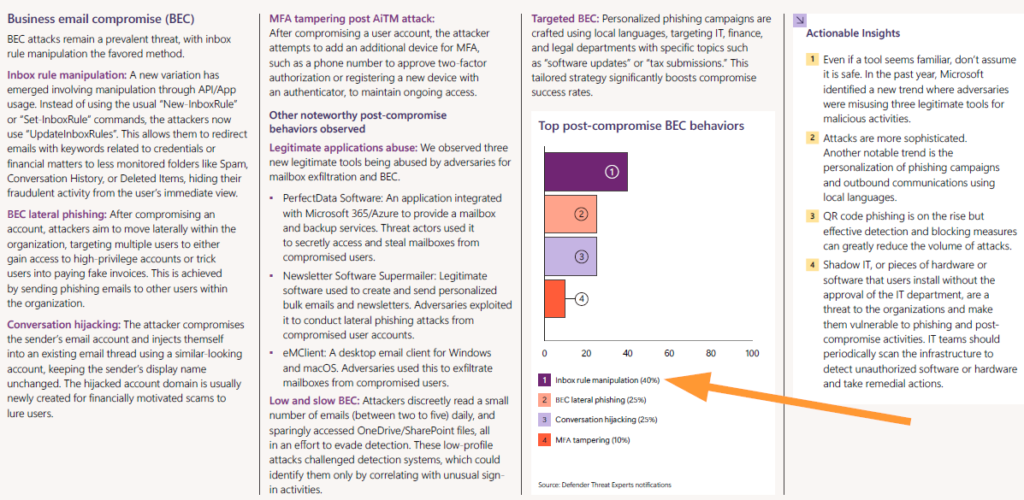
Source: Microsoft Digital Defense Report 2024
We can use a wider search to help find any new inbox rules:
OfficeActivity
| where Operation contains "New-InboxRule"
| where Parameters contains "ForwardTo"
| project TimeGenerated, UserId, Operation, ParametersNow, this will find all the inbox rules, so that might be nice for threat hunting and walking through the data to see what we find, but it’s a bit of a wide net to use with an analytics rule as we would have some low-value entries that are legitimate.
If we expand this query slightly so that we look for inbox rules that forward emails outside of our defined domain, that is much more refined detection to quickly identify emails leaving the business domain:
OfficeActivity
| where Operation contains "New-InboxRule"
| where Parameters contains "ForwardTo"
| where Parameters matches regex "[a-zA-Z0-9._%+-]+@[a-zA-Z0-9.-]+\.[a-zA-Z]{2,}"
| extend ForwardTo = extract("ForwardTo: (.+?)$", 1, Parameters)
| where not(ForwardTo endswith "@yourdomain.com") //Replace with your internal domain****
| project TimeGenerated, UserId, Operation, Parameters, ForwardToOnce we start to narrow in on a potential inbox (Identity though really right because the logged into an account!) we can explore detecting accounts sending an abnormally high volume of messages both internally or externally:
OfficeActivity
| where Operation == "SendOnBehalf" or Operation == "Send" or Operation == "SendAs"
| summarize EmailCount = count() by UserId, RecipientType = iif(RecipientEmailAddresses contains "@yourdomain.com", "Internal", "External"), bin(TimeGenerated, 1h)
| where EmailCount > 100 //Adjust threshold accordingly
| project TimeGenerated, UserId, RecipientType, EmailCount
We can use this query to help us identify those ‘Send on Behalf’ of messages that can be harder to identify when quickly trying to track down what is happening with an inbox compromise.
Thanks for joining us on this KQL based stroll through your o365 Activity log data today! We took a look at how to identify different inbox rules and potential malicious actions. In each of the examples, be sure to update your domain information and to limit the time span you are using to look back in the logs as you explore.
Good luck out there & enjoy your stroll!