Integrating Threat Intelligence in Microsoft Sentinel
Today’s post covers the essential topic of integrating Microsoft threat intelligence within Microsoft Sentinel. In an era where cyber threats are becoming increasingly sophisticated, having a robust strategy to ingest and leverage threat intelligence is crucial for any SOC team. By understanding how to implement and utilize threat intelligence in Sentinel, you can significantly enhance your security posture, enabling faster detection and mitigation of potential threats before they escalate.
We’ll walk through the process of importing threat intelligence, managing and creating threat indicators, and seamlessly integrating this intelligence into KQL queries for advanced analysis. This post aims to provide you with the tools and knowledge to transform your raw data into actionable insights, ensuring your organization stays one step ahead of cyber adversaries.
Let’s dive in and explore how to turn data into your greatest security asset.
Guide to Implement Threat Intelligence in Sentinel
Step 1: Import Threat Intelligence
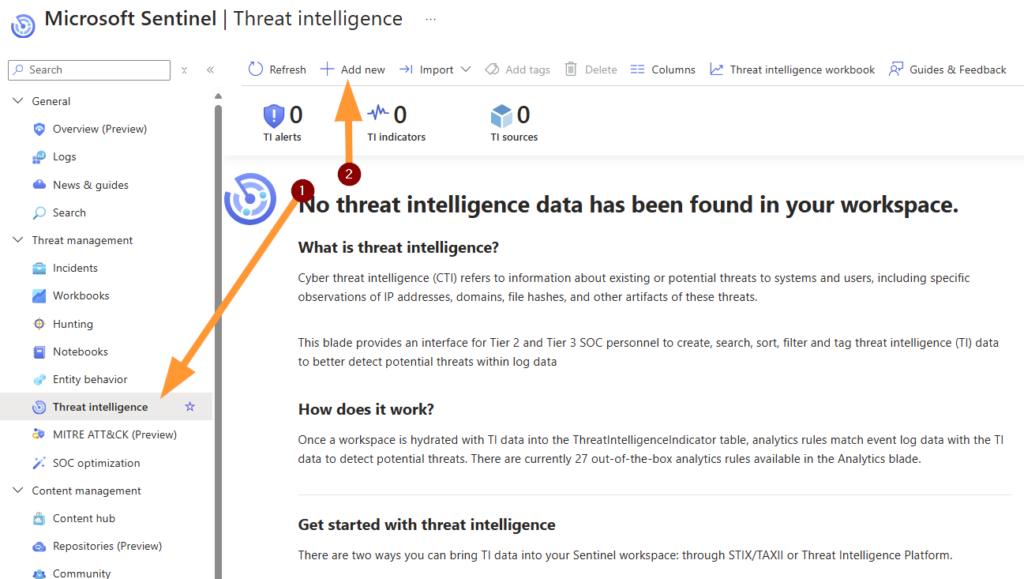
Navigate to Microsoft Sentinel > Log in to the Azure portal and open your Microsoft Sentinel workspace.
From the Sentinel workspace, go to the “Threat Intelligence” page under the “Configuration” section.
Select and enable the relevant data connectors for your threat intelligence sources. This might include connectors for platforms like Anomali, ThreatConnect, or other STIX/TAXII-compatible threat intelligence sources. Many agencies and organizations have policy to define what threat intelligence feeds they are required to implement. Follow the prompts to complete the setup for each connector.
Pro Tip:
It is a common misconception that adding threat intelligence is the end of the story. We also need to take that data and action the indicators!
Step 2: Manage Imported Threat Intelligence
Once the data connectors are enabled, you can view and manage the imported threat intelligence on the Threat Intelligence pane. Here, you will see various threat indicators such as malicious IPs, URLs, and file hashes.
You can also create threat indicators directly within Microsoft Sentinel. This is useful for tagging specific indicators related to ongoing security investigations.
To create a new indicator, click on “Create Indicator” and fill in the required details, such as the indicator type, value, and context.
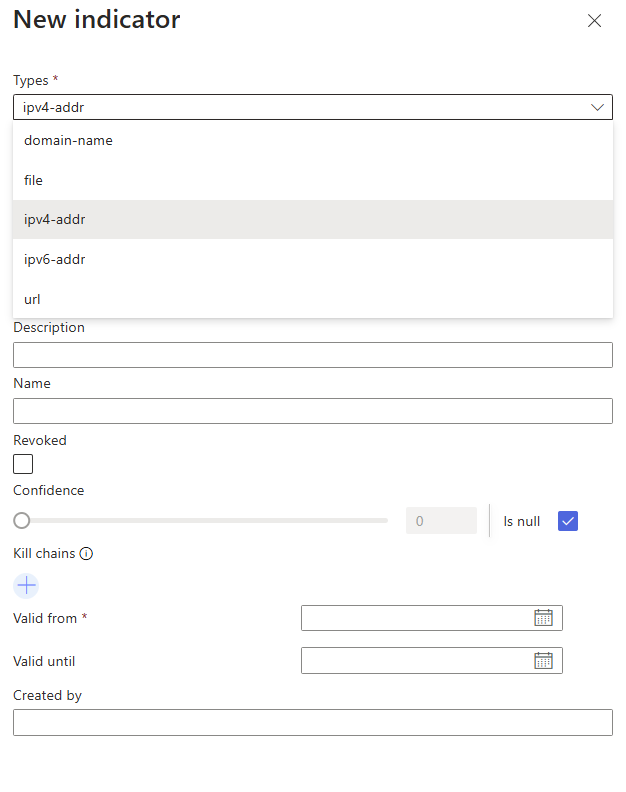
This is how you map the TI feed data coming into your Sentinel instance through the data connector to your other ingested data.
ProTip:
This step is also often overlooked as creating a data connector only brings the data into the Log Analytics workspace for us.
Step 3: Integrate Threat Intelligence into KQL Queries
Open the Log Analytics workspace associated with your Sentinel environment and navigate to the KQL query editor.
Anyone who has worked in Sentinel with me knows that I like to open Log Analytics in a new tab so I can move around quickly and run different types of queries.
Next, let’s write a KQL query to integrate threat intelligence into your analysis. For example, to detect activities from known malicious IP addresses, you can use a query like:
// Replace 'ThreatIntelIndicator' with your threat intelligence table name
SecurityEvent
| where IPAddress in (ThreatIntelIndicator | where IndicatorType == "IP" | project IndicatorValue)
| summarize Count = count() by IPAddress
| sort by Count descThis query joins your SecurityEvent table with the threat intelligence table to identify events involving known malicious IP addresses.
Now, run the query to see the results and validate if the threat intelligence is being correctly integrated. Adjust the query as needed to refine your analysis and ensure it aligns with your security monitoring goals. You may need adjust the ‘ThreatIndicator’ name with your own table name from your configured TI feed.
A More Focused KQL Example
This KQL helps detect and alert on suspicious IP Addresses from the TI feed that are actively attempting to interact with your environment. We would want to have some light edge device or network logs to begin utilizing this TI.
// Get threat intelligence indicators from the TI feed
let ti_indicators = ThreatIntelIndicator
| where IndicatorType == "IP"
| project IndicatorValue;
// Get security events and correlate with TI indicators
SecurityEvent
| where EventID == 4625 // Replace with relevant event ID
| where IPAddress in (ti_indicators)
| summarize Count = count() by IPAddress, Account, bin(TimeGenerated, 1h)
| where Count > 5
| extend AccountCustomEntity = Account, IPCustomEntity = IPAddressSummary
Integrating Microsoft threat intelligence into Microsoft Sentinel is a powerful way to enhance your security operations. Following the steps outlined above, you can import, manage, and utilize threat intelligence to enrich your security data, improve threat detection accuracy, and respond more effectively to potential incidents.
Understanding the value of threat intelligence and how to leverage it within Sentinel ensures that your organization is better prepared to face evolving cyber threats…especially with the rapid pace of AI driven threats where near real-time detection and defense is essential.
Effective integration of threat intelligence provides security teams with the context needed to prioritize alerts and streamline investigations. It enables a proactive approach to security, where known threats are swiftly identified and mitigated before they can cause significant damage.
Additionally, integrating threat intelligence into KQL queries allows for advanced correlation and analysis, providing deeper insights into the threat landscape. You can also utilize existing analytics rules and be able to enhance your existing detections with this near real-time data.
Mastering the integration of threat intelligence into Microsoft Sentinel is a vital step in building a resilient security posture.
Enriching your security data with actionable intelligence, you can transform your defense strategy from reactive to proactive, ensuring your organization stays one step ahead of cyber adversaries. Embrace the power of threat intelligence in Microsoft Sentinel to safeguard your digital assets and maintain a robust security framework in an increasingly complex cyber world.