
Using Threat Intelligence in Microsoft Sentinel to Enhance Incidents
In the ever-evolving landscape of cybersecurity, staying ahead of potential threats requires not just vigilance, but also smart automations. Microsoft Sentinel, our favourite SIEM (Security Information and Event Management) solution, empowers security teams with advanced threat detection and response capabilities. By leveraging Playbooks—automated workflows built on Azure Logic Apps—you can streamline your SOC security operations and respond to incidents faster and with the information your Analysts need to make decisions. A key component of this process is the integration of Threat Intelligence (TI) to enrich incident data with critical context – before anyone opens that incident to investigate.
Integrating Threat Intelligence into your Sentinel Playbooks allows you to automatically look up the risk and reputation of IP addresses (URLs, and other entities) involved in security incidents. This added layer of intelligence can significantly enhance your ability to prioritize and respond to threats, reducing the time to resolution and improving your overall security posture. Expanding automation options can help reduce the existing workloads and have a positive impact on Analyst experiences in Microsoft Sentinel by automating lookups and previously manual steps!
In this article, we explore the detailed steps to set up a Microsoft Sentinel Playbook that uses Threat Intelligence to rank IP addresses involved in an incident; we will also explore changing the Severity of the Sentinel Incident using the same playbook. By following this guide and implementing Threat Intelligence lookups, your security operations are utilizing automation and prioritizing incidents in a proactive fashion – handling potential threats more effectively.
Doing lookups using Threat Intelligence adds definitive information that an Analyst can use right away, in the same Sentinel investigation dashboard without additional clicks. I use the same type of enhanced threat intelligence in incidents that I work with daily. If you are exploring adding automations to your Microsoft Sentinel environment, I encourage you to add a TI lookup to your Sentinel instance and then add more extensive lookups and automations as you get more comfortable!
Step 1: Setting up the Prerequisites
Before integrating VirusTotal into your Playbook, you’ll need to obtain an API key from VirusTotal.
Create an Account: Sign up for a VirusTotal (Free at authoring date) account if you don’t already have one.
Get API Key: Navigate to your VirusTotal account settings and generate an API key.
Activate the API Key: Check out the AzureTracks previous in-depth article here.
Step 2: Creating a Sentinel Playbook
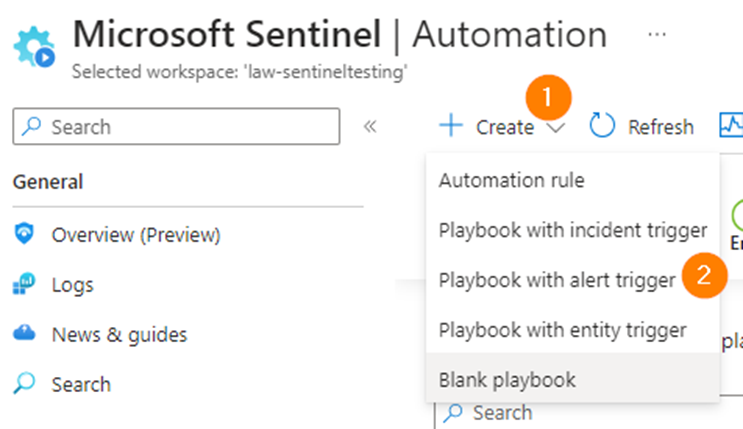
Navigate to Playbooks: In the Sentinel workspace, select “Playbooks” from the left-hand menu and click “Blank Playbook.”
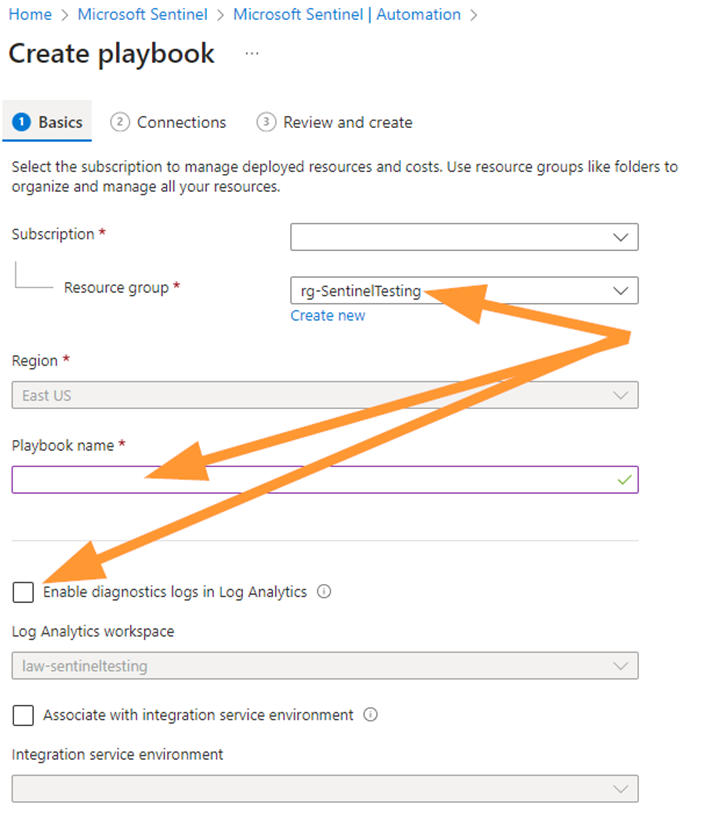
Deploy Logic App: Name your Playbook and select an appropriate resource group. Click “Review + create” and then “Create” to deploy the Logic App.
Step 3: Designing the Playbook
Add a Trigger: Use the “When a response to an Azure Sentinel alert is triggered” as the initial trigger.
Extract Incident Data: Add an action to parse the incident details, extracting the IP addresses involved.
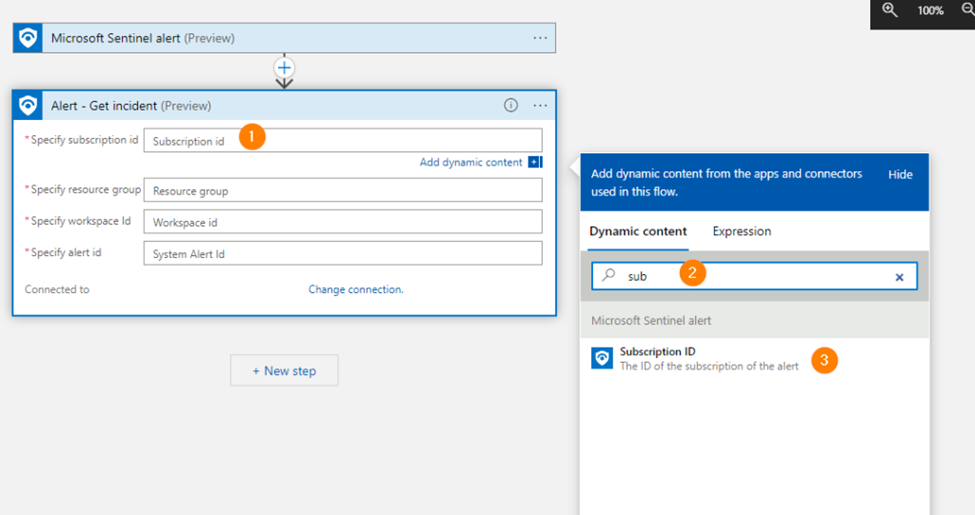
Click on New Step > Choose Microsoft Sentinel and then click on the search field. Enter “get incident” and select that option.
First, select the Specify Subscription ID field, a little pop-up box shows, click in that Search field and start typing “Subscription ID”. When the correct dynamic field appears in the results, select it.
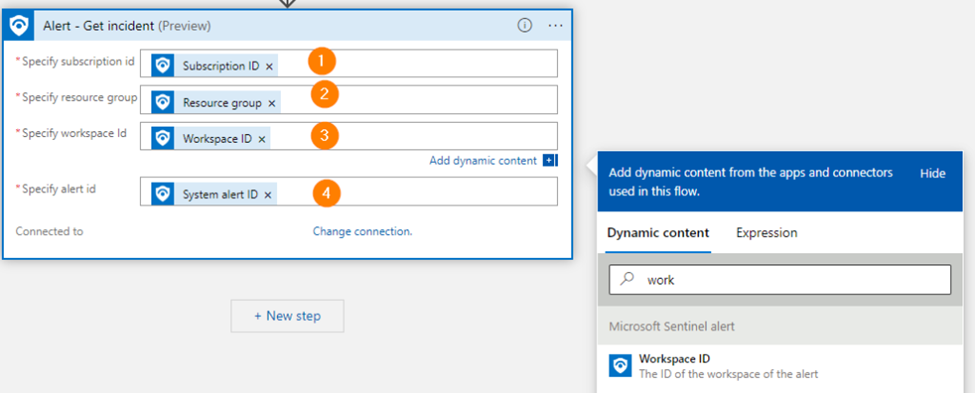
Now for the other fields, make them match:
1. Subscription id
2. Resource group
3. Workspace ID
4. System alert ID
Match the above items in your ‘Get Incident’ action:
Save your Logic App Progress.
Select New Step again and let’s add a Microsoft Sentinel “Entities – Get IPs”. (Preview)
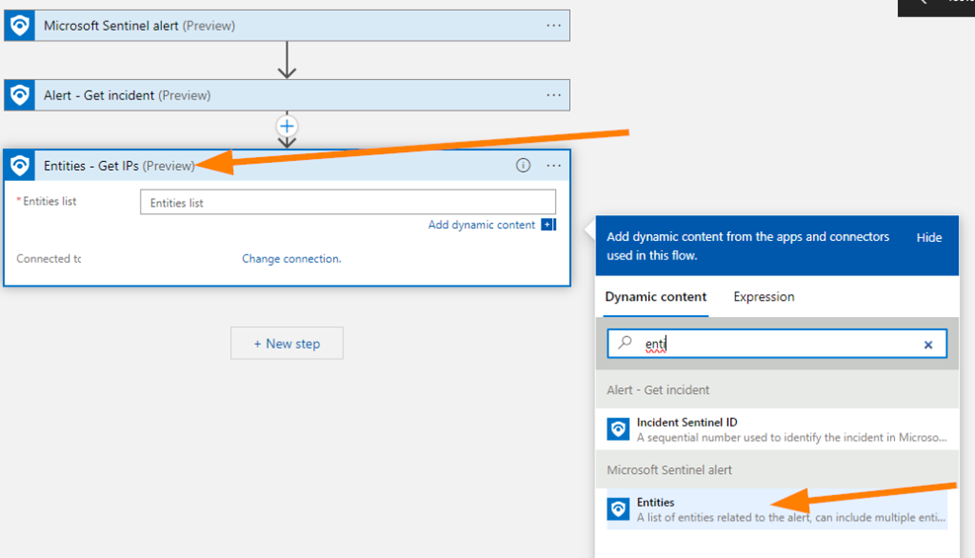
Save your work once more.
Step 4: Integrating VirusTotal API
Add an HTTP Action: Use the “HTTP” action to send a request to the VirusTotal API.
Method: GET
URI: https://www.virustotal.com/api/v3/ip_addresses/{IP Address}
Headers: Include the API key in the headers.
Parse the Response: Add a parsing step to handle the response from VirusTotal, extracting the threat ranking and other relevant data.
Next up, let’s add a New Step > then enter Virus Total in the search field and then select the Virus Total connector.
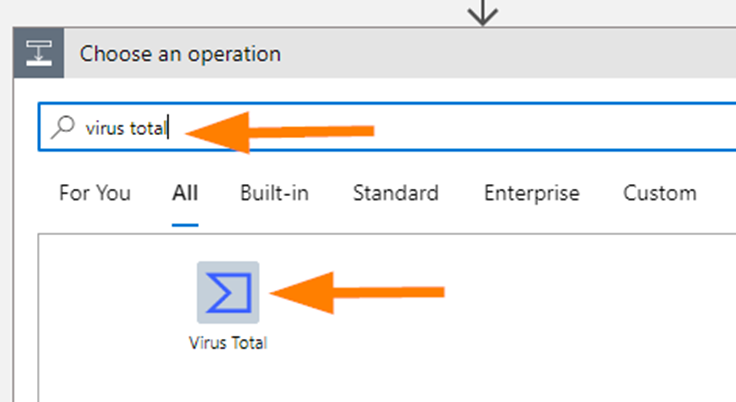
In Select an output, choose IPs.
Now, notice that your logic app automatically created a For Each loop for you.
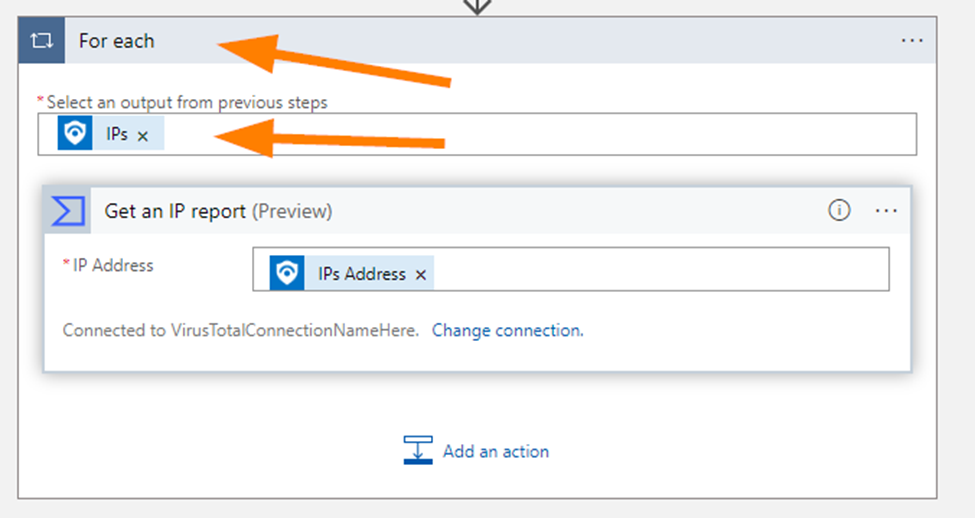
Next, add one more action in the logic app. Add Microsoft Sentinel > Add a Comment.
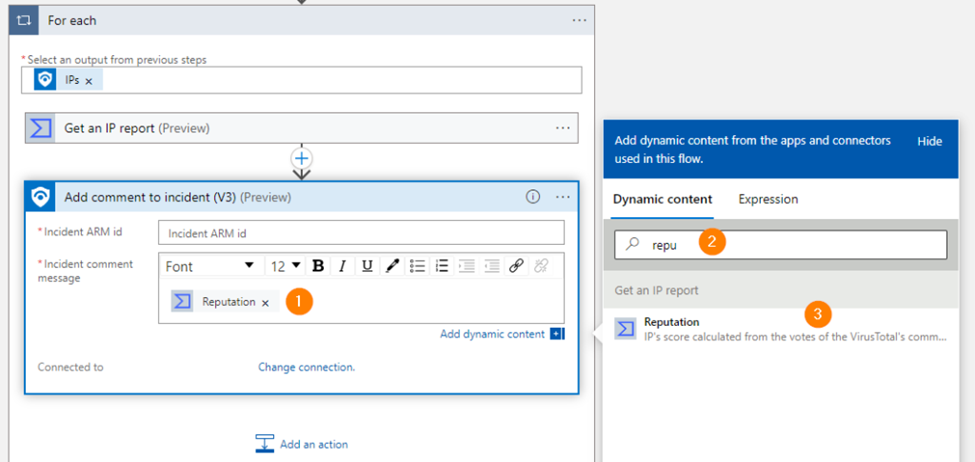
Next, select Reputation > This is the actual result of our VirusTotal lookup via their API on the IP Address we submitted. This will add a comment ‘for each’ IP address we list or submit via our automation, so be aware of consumption.
I usually add additional fields here:
Country, WHOIS, Reputation, Last Analysis Statistics
Step 5: Taking Actions Based on Threat Intelligence
Once you have added a Threat Intelligence ranking, you can use that information to not only add comments, but take some next steps:
Conditional Check:
- Add a condition to check the threat ranking of the IP addresses.
- When High > Change the Sentinel Incident Severity to High.
- Send an Email or alert in Microsoft Teams notifying the Network Team to evaluate or block the IP address.
Send Alerts:
If the ranking is high, use an action to send an alert to your security team via email, Teams, or any other preferred method.
Automated Response:
You can also set actions like isolating the affected endpoint, blocking the IP address, or triggering further investigations.
Wrap-Up
By integrating Threat Intelligence into your Microsoft Sentinel Playbooks, you can significantly enhance your incident response capabilities. This automation helps with quick decision-making, reducing the time to mitigate potential threats.
Deploying such a Playbook ensures that your security operations are not only efficient but also proactive handling incidents. Stay secure and let automation be your ally in the ever-changing landscape of cybersecurity.
For more detailed steps and example configurations, you can refer to the official Microsoft Sentinel documentation and I covered how to add Virus Total specifically in a previous in-depth article here.