
Evaluate Microsoft Defender for Endpoint – Part 1
Completing a comprehensive and independent evaluation of any security product can be complicated and take more time than we really have to spare. Microsoft has provided the ability for all businesses to evaluate Defender for Endpoint on their own through labs and trail licenses! I’ll present some options in my usual walk-through format in a mini-series on how to get started with your evaluation. Take the complexity out and focus on your simulation activities, alerts, and results!
A small baseline first for us — Why are we talking about Defender for Endpoint? That’s a great question! So, we have some excellent security features that we can enforce, centered around Azure features, Azure Active Directory, and SaaS application integration. The endpoint device security is enhanced greatly with Microsoft Defender for Endpoint as we can drive deep integrations and improve security automations, outcomes, and enhancements by utilizing Conditional Access, InTune, Azure AD, and for me a big piece of that puzzle is the Microsoft Defender technologies. As a quick example, below we can see that enforcement of required endpoint state such as current patching levels can integrate with InTune, Azure AD, and then allow or deny access to resources:
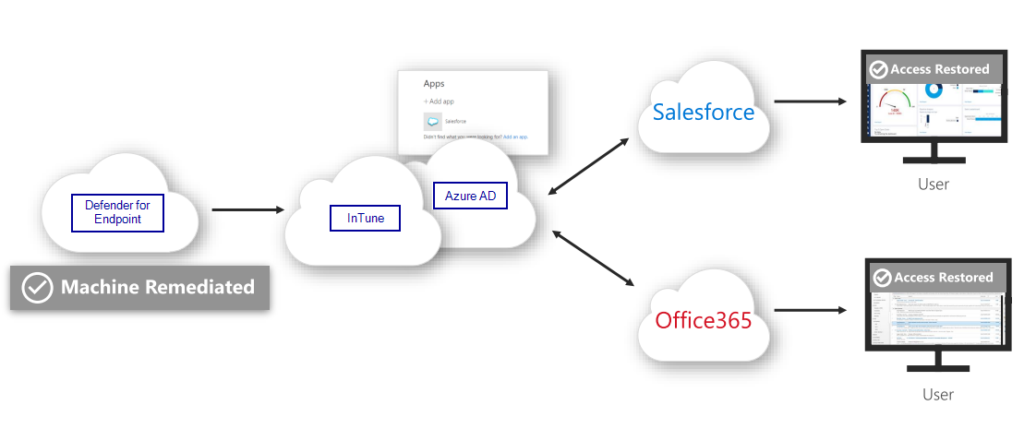
So, to bring a holistic approach to securing identity, endpoint, and data; we are involving all the environments that we work in:
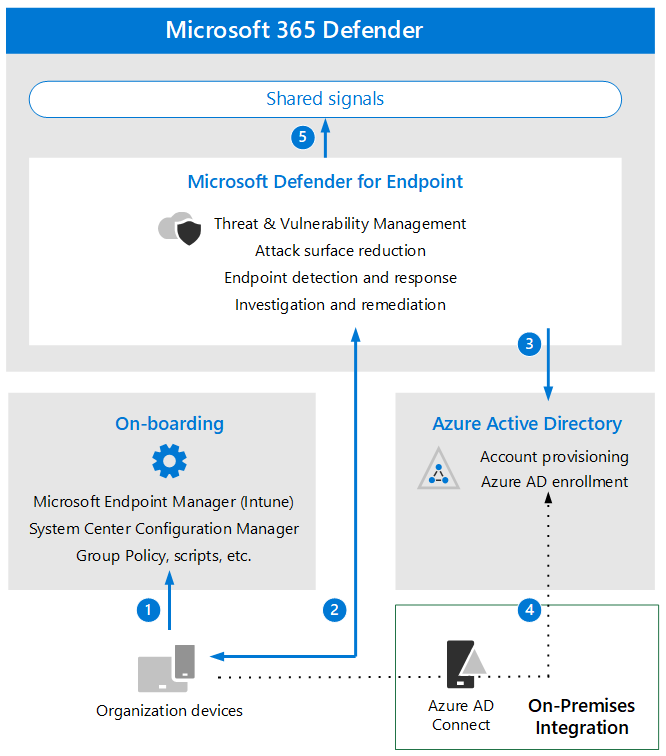
| Callout | Description |
|---|---|
| 1 | Devices are on-boarded through one of the supported management tools. |
| 2 | On-boarded devices provide and respond to Microsoft Defender for Endpoint signal data. |
| 3 | Managed devices are joined and/or enrolled in Azure Active Directory. |
| 4 | Domain-joined Windows devices are synchronized to Azure Active Directory using Azure Active Directory Connect. |
| 5 | Microsoft Defender for Endpoint alerts, investigations, and responses are managed in Microsoft 365 Defender. |
There is so much crossover between endpoint, identity, Microsoft 365, Azure, and on-premises services; that we need to ensure Security Operations has a wide-band of skills, and the ability to gather the security signals needed to gain accurate assessment of risk in an ongoing way.
Anyhow, that’s why we’re here looking at Microsoft Defender for Endpoint to help us all move forwards and improve our security posture.
Alright, let’s move ahead….
First up is some requirements to get us started. We’ll need some licenses for Defender for Endpoint to get us started, so what we need is licenses for our endpoints — if we plan on testing with 3 computers, we will need at least 3 licenses of the following types:
Microsoft Defender for Endpoint requires one of the following Microsoft volume licensing offers:
- Windows 11 Enterprise E5
- Windows 11 Education A5
- Windows 10 Enterprise E5
- Windows 10 Education A5
- Microsoft 365 E5 (M365 E5) which includes Windows 10 Enterprise E5 or Windows 11 Enterprise E5
- Microsoft 365 A5 (M365 A5)
- Microsoft 365 E5 Security
- Microsoft 365 A5 Security
- Microsoft Defender for Endpoint Plan 2
So, you say you don’t have any of these licenses? No worries! Let’s get you all sorted.
Sign up for your free trial here.
Fill out the trial signup form which will be pretty close to what we see here:
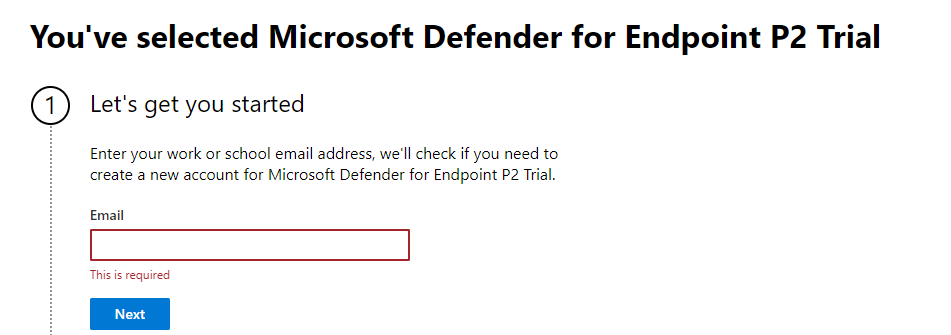
Notice that we have the new naming for the Microsoft Defender for Endpoint product already showing in many places. As a bit of a cheat sheet — check out my previous articles on Ignite November 2021 Security Roundup for all the name changes.
We have 2 skus now for Endpoint protection with Plan 1 being the small business solution with lower pricing and basic EDR and API integration; while Plan 2 has the full soup to nuts coverage we have come to expect with Microsoft Defender for Endpoint security solution software.
Ok, with the labs simplified set-up experience, you can focus on running your own test scenarios and the pre-made simulations to see how Defender for Endpoint performs. You’ll have full access to the capabilities of the Defender for Endpoint platform — such as automated investigations, advanced hunting, and threat analytics, allowing you to test the comprehensive protection stack that Defender for Endpoint offers.
In your own labs experience; you can add Windows 10, Windows 11, Windows Server 2019, or Windows Server 2022 devices that come pre-configured to have the latest OS versions and the right security components in place as well as Office 2019 Standard installed.
Next up, we’ll create the lab, add some devices, and get ready to begin some simulations
In the meantime, consider what roles you would apply in your lab environment. We’ll be using the Security Administrator or Global Administrator roles in our demo, but if we were configuring this for production we would utilize RBAC to support least privilege. Learn more here.
Source: https://docs.micrososft.com