Azure Active Directory Guest Users Configuration
Today we’ll take a look at Azure Active Directory and Guest Users. I wanted to take a few minutes to talk about the common questions that a lot of companies have. With the forced remote working situation world-wide right now, a lot of companies have either jumped into remote user management, or expanded it rapidly. We will look at configuring your Azure tenant Guest accounts to use some improved security that will help protect your organization.
We’ll cover some of the basics without going too deeply into secondary configurations and details. This is intended to get you started, and help improve your configuration if you are just launching your Azure AD services, have jumped in head first, or just want to look at what the deal is.
First, log into your Test tenant. This is really important as we are going to be looking at user authentication changes. Use your Azure Test tenant credentials and log into the Azure portal.
Now browse to Azure Active Directory.
Then click on User Settings.
Now on the blade User Settings, scroll down to External Collaboration Settings.
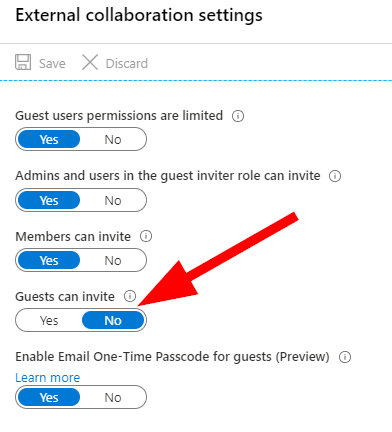
There are a few things to talk about here in External Collaboration Settings:

I want to jump right to the awesome preview feature for ‘Enable One-Time Passcode for Guests (Preview)‘. If you’re anything like me, I saw this and thought it was a perfect addition for Guest account security. We now get the option to force a second factor (2FA) one-time passcode to have a guest account authenticate. Here are the notes:
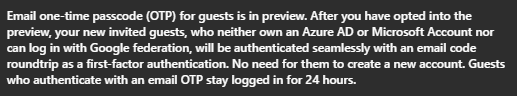
Note that this will only impact new invited guests.
Now, let’s take a look at Collaboration Restrictions at the bottom of this blade. Typically, most companies know their partners and can have IT Security manage approved domains. This is one section where in most cases, we can select Allow Invitations only to the Specified Domains and white-list our allowed collaborators. If it is at all possible, I do recommend that this be set as ‘Allow specified‘ for the best security; but I do also acknowledge that it will need to be managed so please ensure this finds its way into your procedural documentation if you do enable it.
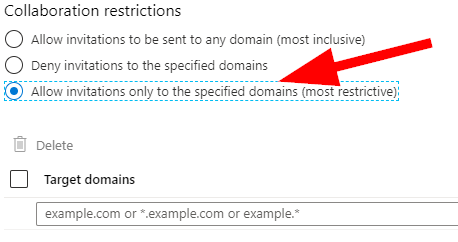
For the remainder of the settings, I typically suggest using some discussion with IT Management and Senior staffers to determine what is right for your own organization; but the typical settings are as follows:
Guest Users Permissions Limited = Yes > This limits the guests ability to get into trouble. Guests are not able to read directories of users, groups, and resources.
Admins and Users in the Guest Inviter Role Can Invite = Yes > This will allow your admins and users that belong to this role to invite others.
Members can Invite = Yes > This one is important. This is the setting that allows your users to invite others to resources such as SharePoint Online sites in Office 365 for collaboration.
Guest can Invite = No> This one is important as well. This is the setting that can allow a Guest account to invite other Guests. We almost always want to have this set to No. This can help prevent data exfiltrations by restricting account invites right out of the gate. Easy win to set this to No.
We have already covered the other settings, so go ahead and Save. Now, using a Private Session in Edge Chromium or your other favourite browser, go create a guest user and test out your settings!
Note: I’ve noticed in these extremely busy times with Azure resources, that it can take a full 1hour + to propagate settings depending on what you change and what region your tenant is in; so please enjoy a lovely cup of coffee or tea or review some other settings while waiting!